4학년 1학기에 Information Security 수업을 듣고, 정리한 내용이다.
Necessities of cryptographic tools for Information Security
- 네트워크 보안과 시스템 보안을 위해!
- Network Security
- cryptographic tools is fundamental function of the network security to make the communication secure
- public network, 즉 예를 들어 같은 와이파이로 서로에게 정보를 공유할 경우 해킹당할 위험이 있음
- 이때 secure하게 정보를 전송할 수 있는 방법 → use cryptographic tools(encode message, decode ciphertext)
- System Security
- securing for our computer machine → can protect data in memory and storages by using cryptographic tools
- 보안 기술이 필요함. 해커가 데이터가 저장된 server를 접속 못하게 하기 위해서
Confidentiality with Symmetric Encryption
Symmetric Encryption
- The universal technique for providing confidentiality for transmitted or stored data
- Also referred to as conventional encryption or single-key encryption
- Two requirements for secure use
- Need a strong encryption algorithm
- Sender and receiver must have obtained copies of the secret key in a secure fashion and must keep the key secure
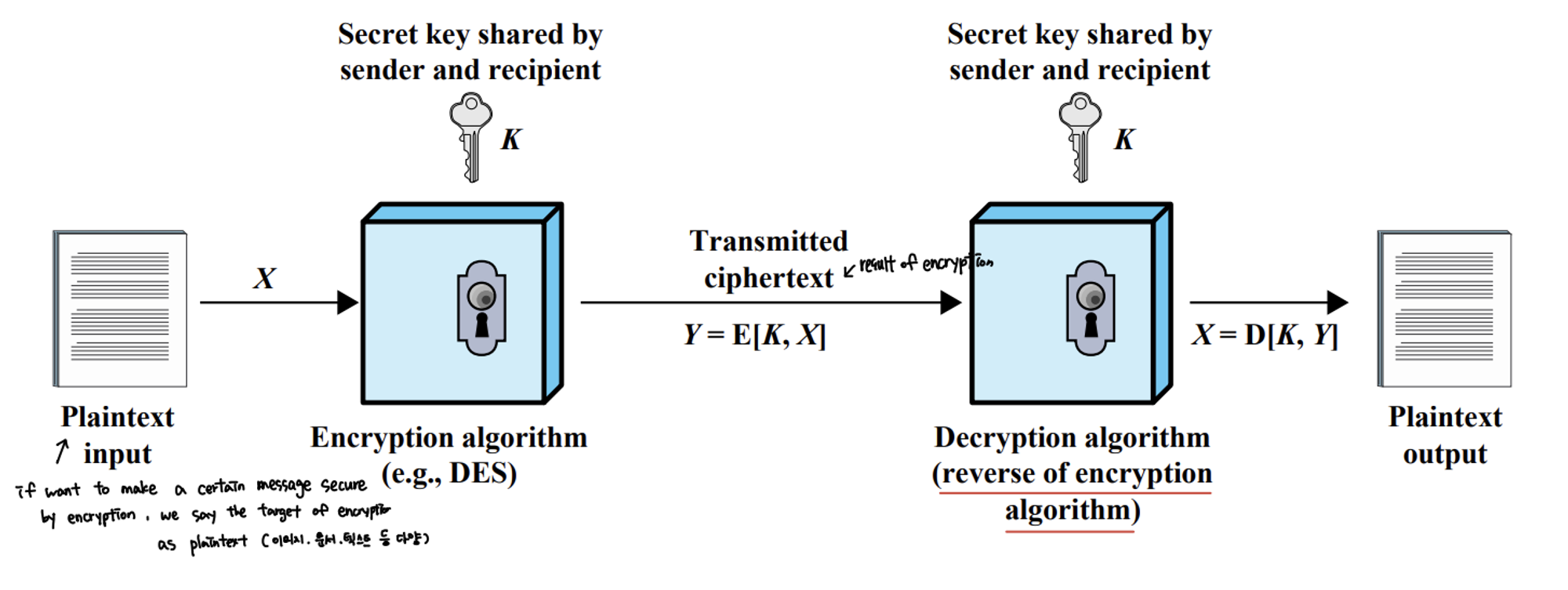
1. Simplified Model of Symmetric Encryption
- 3개를 고려
- how can generate key
- how can encrypt plaintext
- how to decrypt ciphertext
2. Attacking Symmetric Encryption
- Cryptanalytic Attacks
- Rely on
- Nature of the algorithm → attacker analyze the structure of algorithm carfully to detect weak things
- Some knowledge of the general characteristics of the plaintext (blackbox attack)
- 예: sender가 오직 0,1을 메세지로 보내는 경우 암호화과정을 쉽게 예측 가능
- Some sample plaintext-ciphertext pairs (blackbox attack)
- Exploits the characteristics of the algorithm to attempt to deduce a specific plaintext or the key being used
- Rely on
- Brute-Force Attack
- Try all possible keys on some ciphertext until an intelligible translation into plaintext is obtained → On average half or all possible keys must be tried to achieve success
3. Block & Stream Ciphers
-
Block Cipher
- Processes the input one block of elements at a time
- Produces an output block for each input block
- Can reuse keys
- More common
-
Stream Cipher
- Processes the input elements continuously, Encrypts plaintext one byte (or bit) at one time
- Produces output one element at a time
- Primary advantage is that they are almost always faster and use far less code
Symmetric Block Encryption Algorithms
Data Encryption Standard(DES)
- The most widely used encryption scheme
- = DEA(Data Encryption algorithm)
- Uses 64 bit plaintext block, 56 bit key to produce a 64 bit ciphertext block
- Strength concerns:
- Use of 56 bits key → easy to perform brute-force attack
Triple DES(3DES)
- Repeats basic DES algorithm three times using either two or three unique keys
- First standardized for use in financial applications in ANSI standard X9.17 in 1985
- Attractions
- 168-bit key length overcomes the vulnerability to brute-force attacks of DES
- Underlying encryption algorithm is the same as in DES
- main components of triple DES is DES
- Drawbacks
- Algorithm is sluggish in software
- 알고리즘이 소프트웨어에서 느리게 동작함(DES를 3번 반복하므로, DES가 한번 실행할 때 소용되는 시간의 3배가 걸림)
- Uses a 64bit block size
- Algorithm is sluggish in software
Advanced Encryption Standard(AES)
- 3DES의 replacement
- 3DES was not reasonable for long term use
- Have a security strength equal to or better than 3DES and significantly improved efficiency
- 128 bit data and 128/192/256 bit keys
Practical Security Issues
- Typically symmetric encryption is applied to a unit of data larger than a single 64-bit or 128-bit block
- How can we encrypt longer messages?
- Divide the message to shorter chunks and encrypt each with the same key
- Electronic codebook(ECB) mode
- same key일 때, plaintext가 같으면 ciphertext가 같을 것 → security problem(Attacker may be able to exploit regularities in the plaintext)
- (Other) Mode of operations (해결책으로 나옴)
- Alternative techniques developed to increase the security of symmetric block encryption for large sequences
- Overcomes the weaknesses of ECB
- Divide the message to shorter chunks and encrypt each with the same key
Message Authentication and Hash Functions
Message Authentication의 필요성
- Protects against active attacks
- public network를 통해 message를 전송할 때, attacker가 message를 modification하는 걸 막기 위함
- Verifies received message is authentic
- Contents have not altered
- From authentic source
- Timely and in correct sequence
- Can use conventional(=symmetric)encryption
- only sender&recevier share a key
Message Authentication without Message Encryption
- Message encryption by itself does not provide a secure for of authentication
- Situations in which message authentication without confidentiality may be preferable include:
- There are a number of applications in which the same message is broadcast to a number of destinations
- An exchange in which one side has a heavy load and cannot afford the time to decrypt all incoming messages
- Authentication of a computer program in plaintext is an attractive service
- There is a place for both authentication and encryption in meeting security requirements
Authentication Using Symmetric Encryption
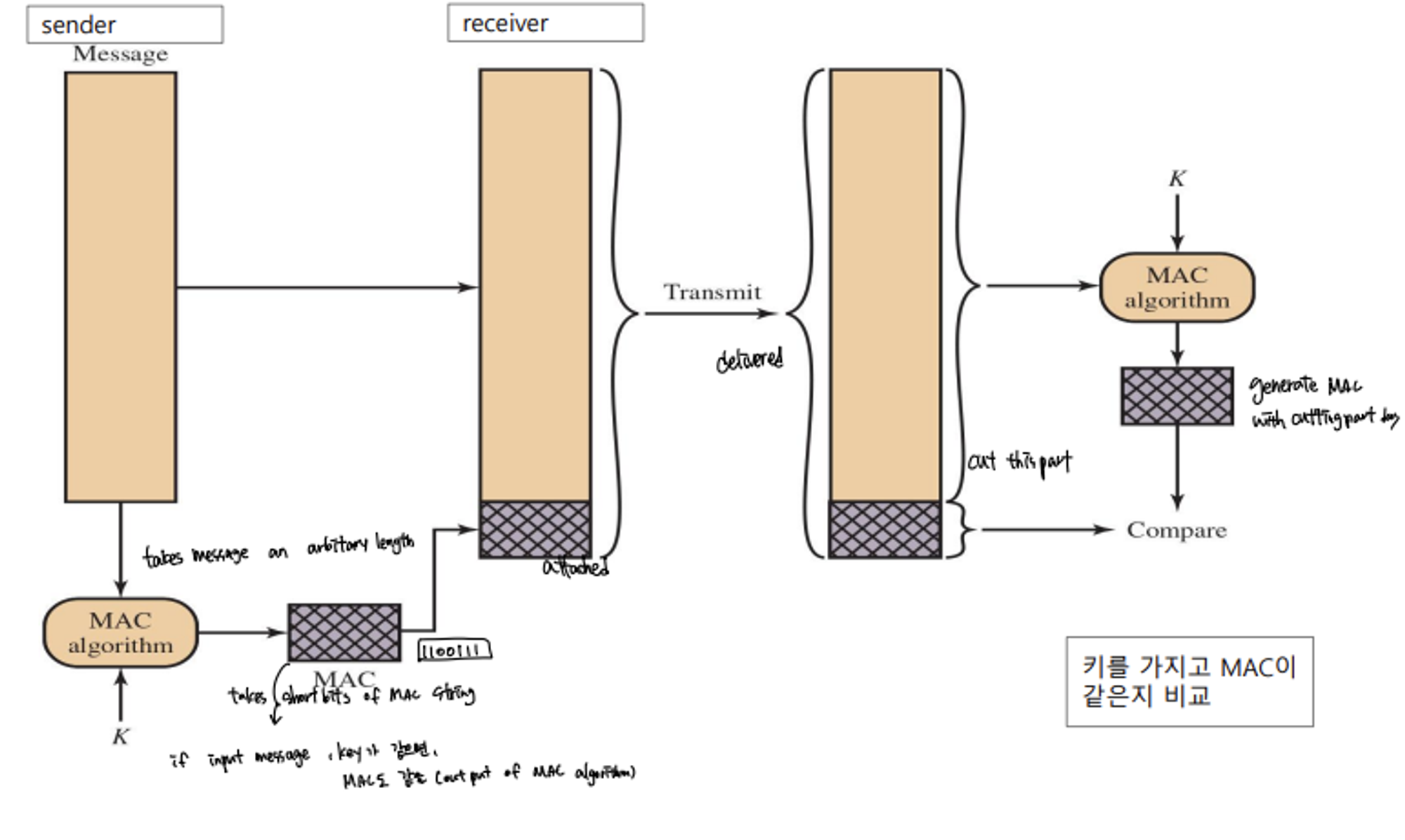
Message Authentication Using a Message Authentication Code
- compose of two algorithm
- key generation algorithm
- MAC algorithm
- Process
- MAC is generated from MAC algorithm by input Message and Key
- MAC is attached to original message, and then transimitted to recevier
- Receiver divide the transmitted message into MAC part, Messge part
- Receiver generate code from MAC algorithm by input Message part and shared key
- And then compare the code to the MAC code
- If they are same, message is not altered
Secure Hash Functions
Hash Function Requirements
- Can be applied to a block of data of any size
- Produces a fixed-length output
- H(x) is relatively easy to commpute for any given x
- One-way or pre-image resistant: Computationally infeasible to find x such that H(x)=h
- Weak collision resistant(Second preimage resistance): Computatinally infeasible to find y≠x such that H(y)=H(x)
- Strong collision resistance: Computationally infeasible to find any pair (x,y) such that H(x)=H(y)
Security of Hash Functions
- Two approach to attacking a secure hash function
- Cryptananalysis
- exploit logical weakness in the algorithm
- Brute-force attack
- Strength of hash function depends solely on the length of hash code produced by the algorithm
- Cryptananalysis
- SHA is most widely use hash algorithm
- Other Applications of Hash Functions
- Passwords
- Hash of a password is stored by an operating system
- Intrusion detection
- Store H(F) for each file on a system and secure the hash values
- Passwords
Public Key Encryption
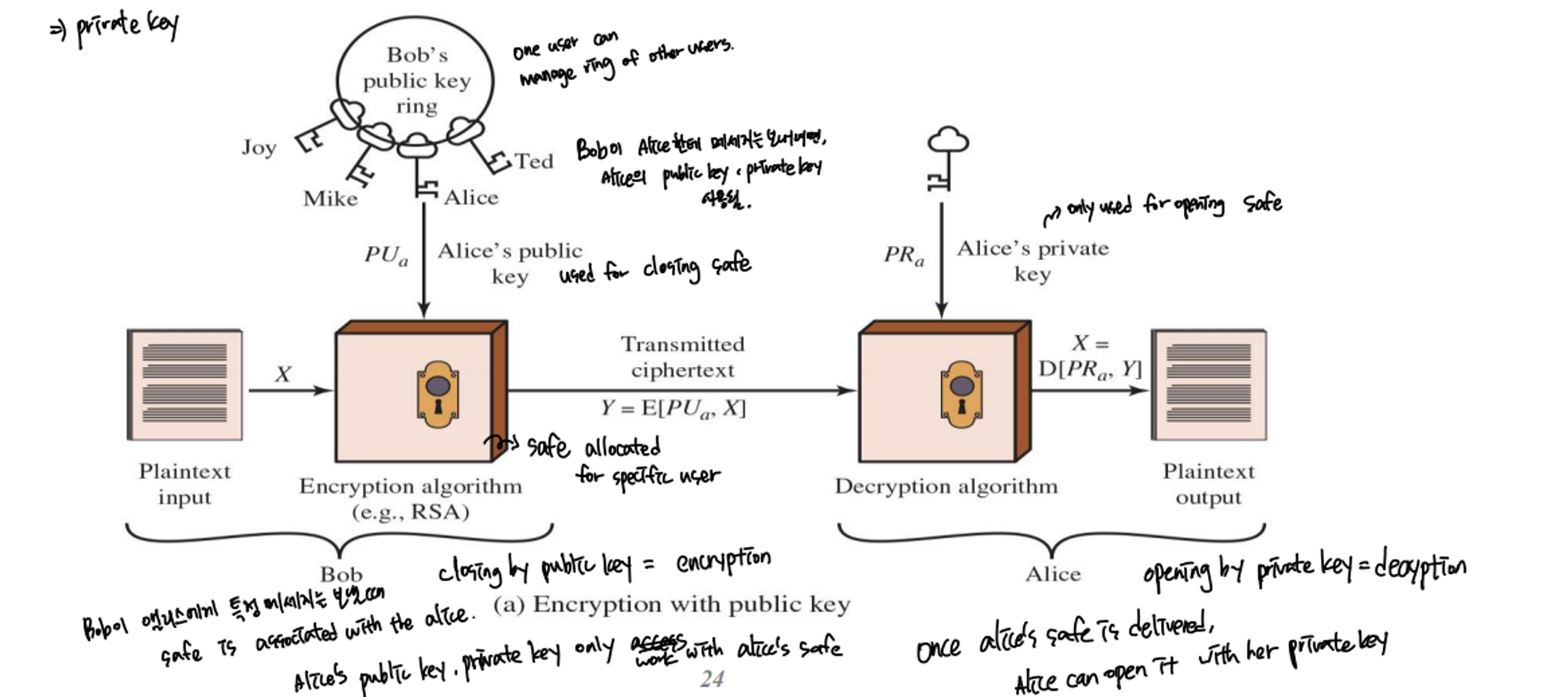
Public Key Encryption Structure
- publicly proposed by Diffie and Hellman in 1976
- Based on mathematical functions
- Asymmetric
- Uses two seperate keys: Public key and private key
- Public key is made public for others to use
- Some form of protocol is needed for distribution
Environment
- plaintext
- Encryption algorithm
- Public and private key
- Ciphertext
- Decryption key
- 설명: Bob이 Alice에게 message를 보내려면, Alice의 public key, private key가 사용됨. Alices’s safe is closing by Alice’s public key = encryption, once alice’s safe is delivered, Alice can open it with her private key (decryption)
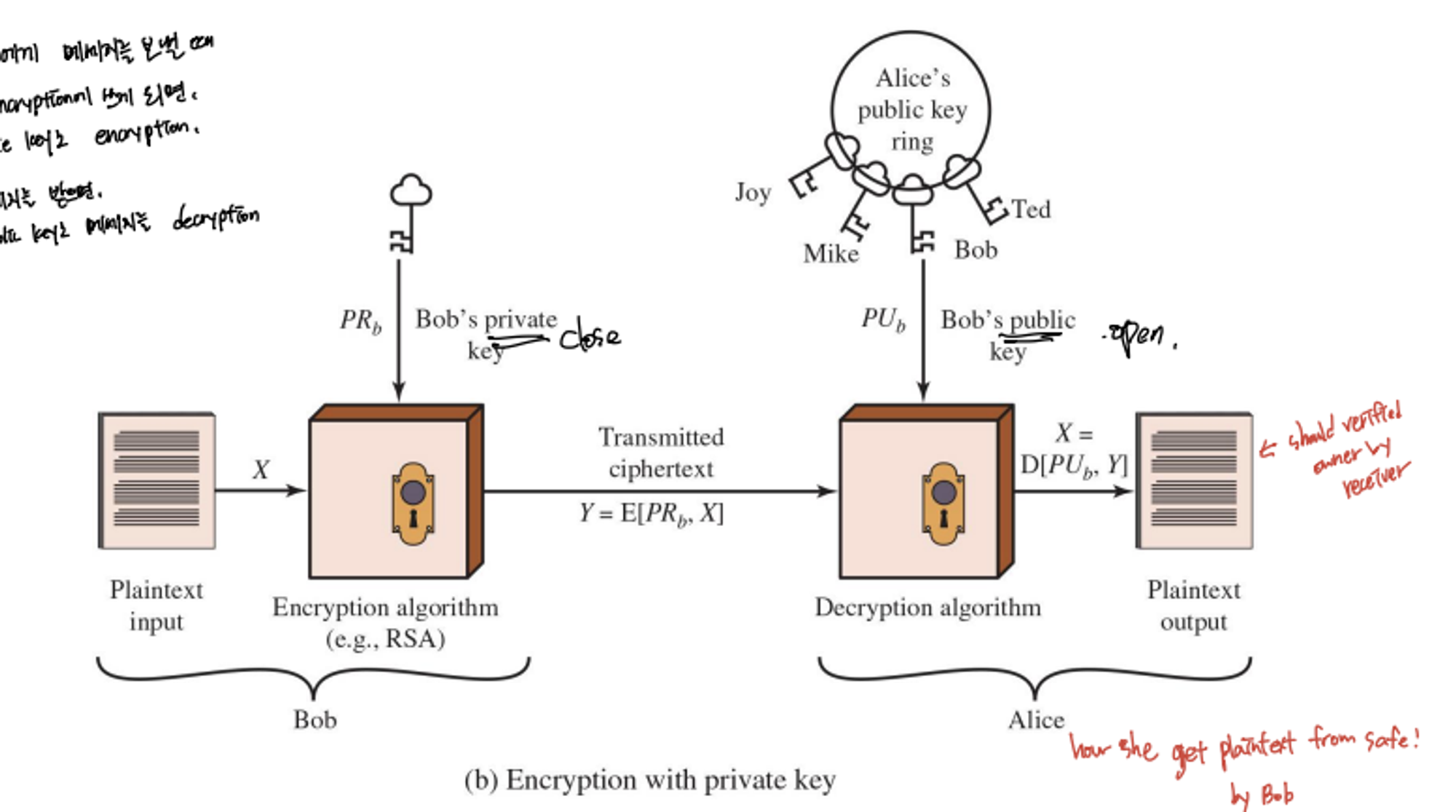
Digital Signature
- User encrypts data using his or her own private key
- Anyone who knows the corresponding public key can decrypt the message
- 설명: Bob이 Alice에게 메시지를 보낼 때 private key를 encryption에 쓰게 되면, Bob의 private key로 encryption, Alice가 메시지를 받으면, Bob의 public key로 메시지를 decryption
Requirements for Public Key Cryptosystems
- Computatinally easy to create key pairs
- Computationally easy for sender knowing public key to encrypt messages
- Computationally easy for receiver knowing private key to decrypt ciphertext
- Computationally infeasible for opponent to determine private key from public key
- Computationally infeasible for opponent to otherwise recover original message
- Useful if either key can be used for each role
Asymmetric Encryption Algorithms
RSA
- Developed in 1977
- Most widely accepted and implemented approach to public-key encryption
- Block cipher in which the plaintext and ciphertext are integers between 0 and n-1 for some n
Diffie-Hellman key exchange algorithm
- Enables two users securely reach agreement about a shared secret that can be used as a secret key for subsequent symmetric encryption of messages
- Limited to the exchange of the keys
Digital Signature Standard(DSS)
- Provides only a digital signature function with SHA-1
- Cannot be used for encryption or key exchange
Elliptic curve crypography
- Security like RSA, but with much smaller keys
- requires small size of key and generate small size of blocks compared to RSA
Digital signatures and Key management
Digital Signature
- Used for authenticating both source and data integrity
- Create by encrypting hash code with private key
- Does not provide confidentiality
- 디지털 서명의 핵심 목적은 메세지의 무결성과 발신자의 인증을 보장하는 것으로 이는 메시지를 암호화하여 서명하는 과정을 통해 이루어짐. 그러나 디지털 서명 과정 자체는 메세지의 내용을 숨기는데 초점을 두지 않음
- Even in the case of complete encryption, message is safe from alternation but not eavesdropping
- 메시지가 변경되지 않았다는 사실과 발신자가 누구인지는 보장할 수 있지만, 메시지 자체가 암호화 되지 않을 경우 제 3자가 메시지를 엿볼 수 있음
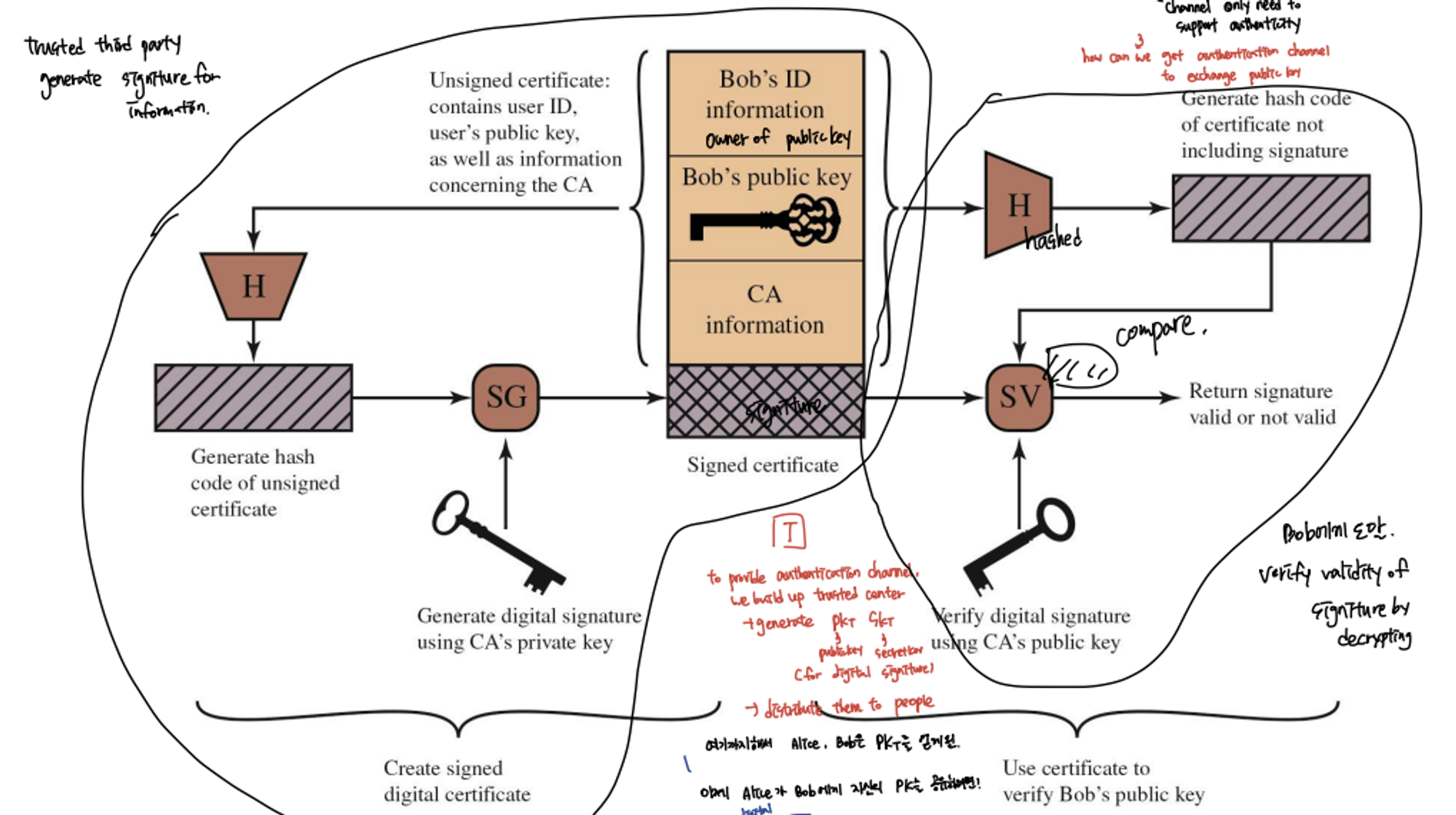
Public Key Certificates (공개키 인증서)
- Bob이 Alice에게 public key를 공유할 때 channel only need to support authenticity → how can we get authentication channel to exchange public key → CA provide public key certificate
- 과정
- To provide authentication channel, third party center(public key certificate) generate PKi, SKi and distribute them to people
- Alice, Bob get their PKi, SKi
- 이제 Bob가 Alice에게 자신의 public key를 공유하려면?
- Bob가 CA에 자신의 PK를 보냄
- CA는 generate digital signiture of PK by using CA’s private key
- Then, Bob trasmit PK with digital signiture to Alice
- After Alice recieved, compare them
- Alice verified digital signiture by CA’s public key
- Generte hash code of certificate not including digital signiture
- If they are same, Bob’s public key is valid
▪ Symmetric Key Exchange Using Public Key Encryption
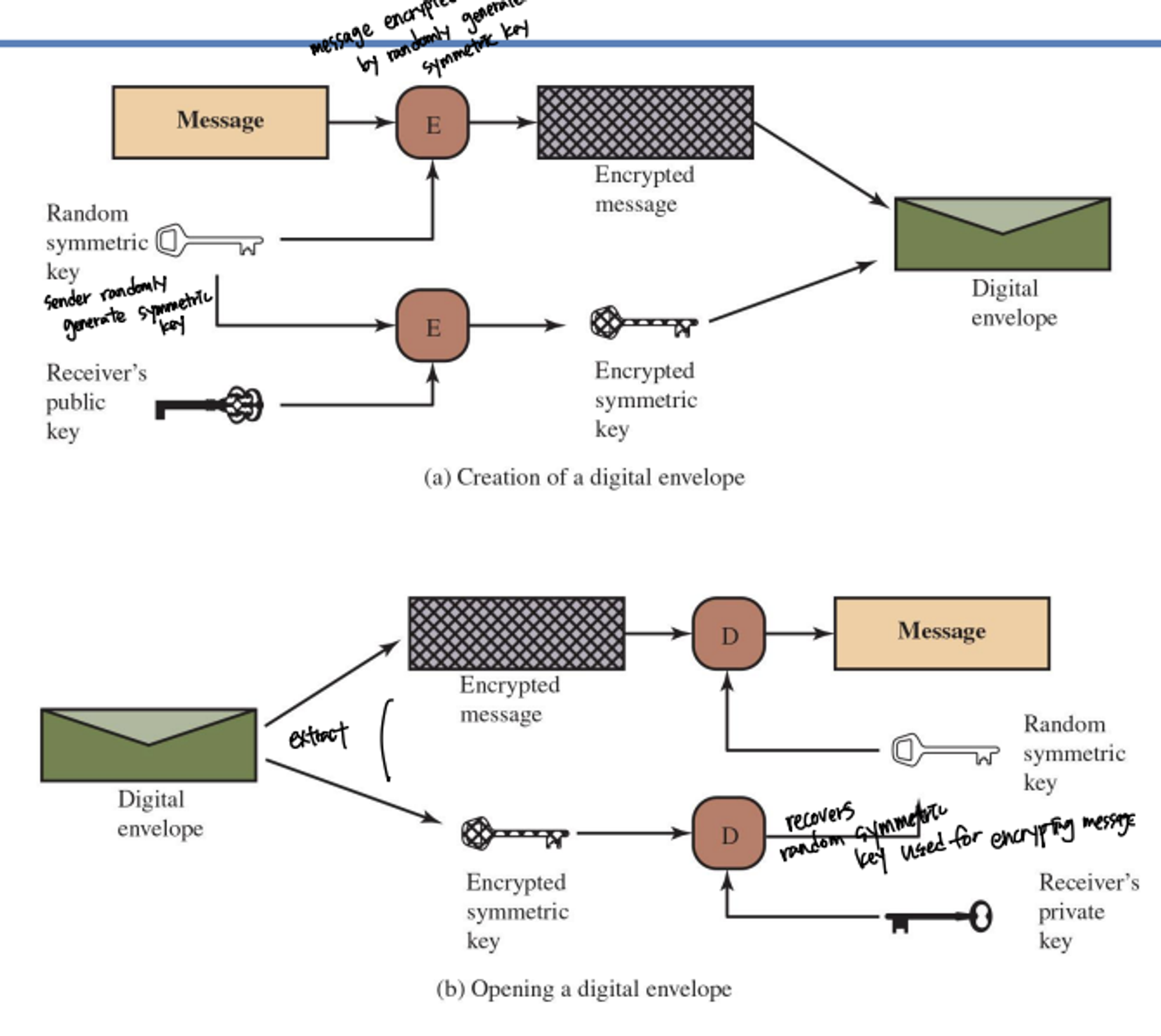
Digital Envelopes
- utilizes advantage of aymmetric encryption and public key encryption
- Protects a message without needing to first arrange for sender and receiver to have the same secret key
- equates to the same thing as a sealed envelope containing an unsigned letter
- 과정
- Creation of a digital envelope
- Sender randomly generate symmetric key
- Random symmetric key and Receiver’s public key is encrypted by encryption algorithm
- Message is encrypted by using random symmetric key
- Digital envelop is created by consisting encrypted message and encrypted symmetric key
- Opening a digital envelope
- Encrypted message and encrypted symmetric key are extracted by digital envelope
- get random symmetric key by decrypting encrypted symmetric key by using receiver’s private key
- get plain message by decrypting encrypted message by using random symmetric key
- Creation of a digital envelope
Random and Pseudorandom Numbers
The Use of Random Numbers
- Used to generate keys for public-key algorithms
- To generate stream key for symmetric stream cipher
- To generate symmetric key for use as a temporary session key or in creating a digital envelope
- Handshaking to prevent replay attacks
- To generate session key
Random verses Pseudo rando
- Random takes alot of cost and slow
- 예측 가능성: 진짜 난수는 예측할 수 없는 반면, 유사 난수는 결정적 알고리즘을 사용하므로 원리적으로 예측 가능합니다(시드 값이 알려지면)
- 효율성: 유사 난수 생성은 일반적으로 진짜 난수 생성보다 훨씬 빠르고 효율적입니다.
- 응용: 보안이 중요한 암호학적 응용에서는 예측할 수 없는 진짜 난수가 선호되지만, 대량의 난수가 필요한 시뮬레이션 같은 경우에는 유사 난수가 더 적합할 수 있습니다.