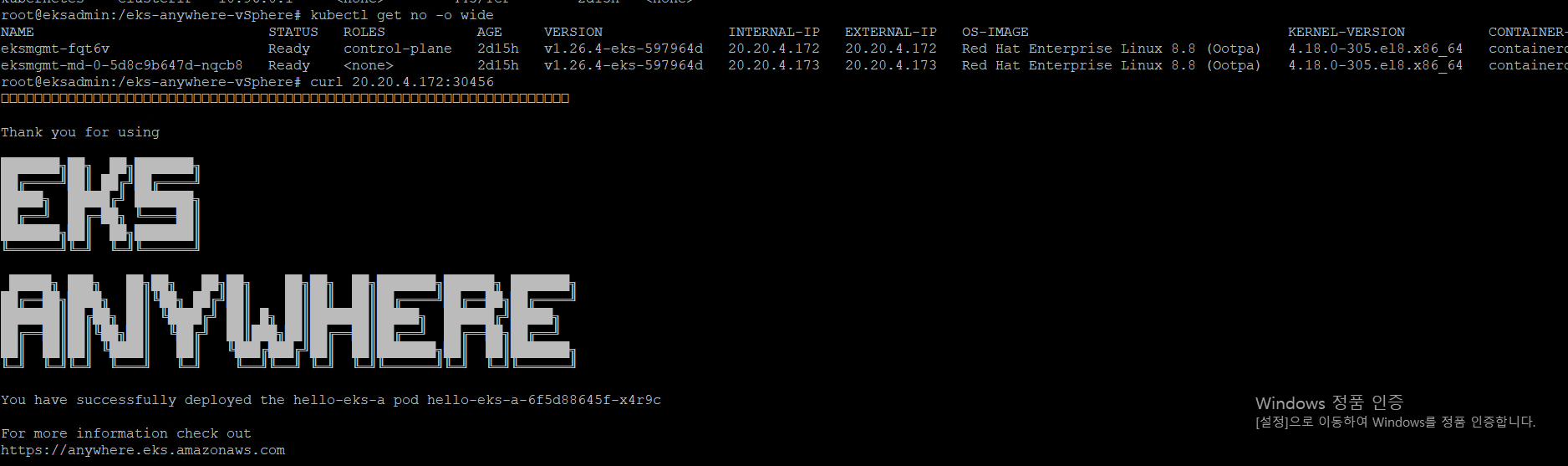
참고링크
https://velog.io/@hyeseong-dev/Harbor-소개-설치-및-배포
https://velog.io/@nohsangwoo/폐쇄망-docker설치
https://ploz.tistory.com/entry/17-docker-Private-RegistryHarbor-설치-및-Portainer-연동
https://zunoxi.tistory.com/130
폐쇄망에서... eks anywhere 설치는 진짜 힘들다...
패키지 인스톨 다시 설치 안되고ㅠ큐ㅠ 큐레이티드 패키지 안되고 ㅠㅠ (폐쇄망 설치 하지마세요... 지옥 on 2023년 06월부로는 제대로 되지 않습니다. 억지로 하면 할수있는데, 그게 과연 eks anywhere 가 맞을까요? ㅠㅠ )
EKSCTL download
# brew 설치
sudo yum update
sudo yum install git-all
# https://qiita.com/blackpeach7/items/c61c3e3d1acddbe36114
/bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install.sh)"
export PATH=/home/linuxbrew/.linuxbrew/bin:$PATH
brew -v
# eks-anywhere 설치
brew install gcc
brew install yq
curl "https://github.com/weaveworks/eksctl/releases/latest/download/eksctl_$(uname -s)_amd64.tar.gz" \
--silent --location \
| tar xz -C /tmp
sudo mv /tmp/eksctl /usr/local/bin/
# docker 설치
sudo amazon-linux-extras install -y docker
sudo systemctl start docker
sudo systemctl enable docker
sudo usermod -aG docker $USER
sudo chmod 666 /var/run/docker.sock
docker info
# EKS anywhere cluster download
eksctl anywhere download artifacts
eksctl anywhere download images -o images.tar
eksctl anywhere import images -i images.tar -r <registryUrl> \
-- bundles ./eks-anywhere-downloads/bundle-release.yaml
Harbor
curl -s https://get.docker.com | sudo sh
curl -L https://github.com/docker/compose/releases/download/1.24.1/docker-compose-`uname -s`-`uname -m` -o /usr/local/bin/docker-compose
chmod +x /usr/local/bin/docker-compose
ln -s /usr/local/bin/docker-compose /usr/bin/docker-compose
docker-compose -version
wget https://github.com/goharbor/harbor/releases/download/v1.10.1/harbor-offline-installer-v1.10.1.tgz
cd harbor
vim harbor.yaml
# change IP, remove 443 ( I reckon that we dont use 443, No internet env )
systemctl restart docker
./install.sh
sudo docker-compose down -v
sudo docker-compose down -v
openssl genrsa -out ca.key 4096
openssl req -x509 -new -nodes -sha512 -days 3650 \
-subj "/C=KR/ST=Seoul/L=Seoul/O=mzc/OU=mzc/CN=eksanywhere.com" \
-key ca.key \
-out ca.crt
openssl genrsa -out eksanywhere.com.key 4096
openssl req -sha512 -new \
-subj "/C=KR/ST=Seoul/L=Seoul/O=mzc/OU=mzc/CN=eksanywhere.com" \
-key eksanywhere.com.key \
-out eksanywhere.com.csr \
-addext
echo subjectAltName = IP:13.125.9.9 > extfile.cnf
openssl x509 -req -days 365 -in mzc.com.csr -CA ca.crt -CAkey ca.key -CAcreateserial \
-out mzc.com.cert -extfile extfile.cnf
cat > v3.ext <<-EOF
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[alt_names]
DNS.1=eksanywhere.com
DNS.2=eksanywhere
DNS.3=hostname
EOF
echo subjectAltName = IP:13.125.9.9 > extfile.cnf
openssl x509 -req -days 365 -in mzc.com.csr -CA ca.crt -CAkey ca.key -CAcreateserial \
-out mzc.com.cert -extfile extfile.cnf
/etc/docker/certs.d/ip:port/ca.crt
https:
# https port for harbor, default is 443
port: 443
# The path of cert and key files for nginx
certificate: /home/ubuntu/pki/eksanywhere.pem
private_key: /home/ubuntu/pki/eksanywhere.pem
./install.sh
EKS Anywhere
https://docs.docker.com/engine/security/certificates/
sudo dpkg -i ./containerd.io_1.2.13-2_amd64.deb \
./docker-ce_19.03.103-0ubuntu-focal_amd64.deb \
./docker-ce-cli_19.03.103-0ubuntu-focal_amd64.deb \
./docker-buildx-plugin_0.10.2-1ubuntu.20.04focal_amd64.deb \
./docker-compose-plugin_2.10.2~ubuntu-focal_amd64.deb
# Making harbor project
eksctl anywhere download artifacts
tar -xvf eks-anywhere-downloads.tar.gz
eksctl anywhere download images -o images.tar
export REGISTRY_ENDPOINT=ip:port
export REGISTRY_USERNAME=admin
export REGISTRY_PASSWORD=Harbor12345
eksctl anywhere download artifacts
tar -xzf eks-anywhere-downloads.tar.gz
eksctl anywhere download images -o eks-anywhere-images.tar
docker login ip:port
eksctl anywhere import images -i eks-anywhere-images.tar --insecure --bundles eks-anywhere-downloads/bundle-release.yaml --registry ip:port
docker ca 설정해도 계속 지속적으로 헬름에서 오류가 나서 insecure 추가 했음
bundle-release.yaml에 public ecr을 전부 registry로 바꿔주었음 ( :%s/public.ecr.aws/${registry ip}/g
docker pull quay.io/jetstack/cert-manager-cainjector:v1.11.0
docker pull quay.io/jetstack/cert-manager-controller:v1.11.0
docker pull quay.io/jetstack/cert-manager-webhook:v1.11.0
docker pull ghcr.io/kube-vip/kube-vip:v0.5.12
docker pull ghcr.io/kube-vip/kube-vip:v0.4.2
docker pull quay.io/k8scsi/csi-node-driver-registrar:v2.0.1
docker pull gcr.io/cloud-provider-vsphere/csi/release/driver:v2.1.0
docker pull quay.io/k8scsi/livenessprobe:v2.1.0
docker pull quay.io/k8scsi/csi-attacher:v3.0.0
docker pull gcr.io/cloud-provider-vsphere/csi/release/driver:v2.1.0
docker pull quay.io/k8scsi/livenessprobe:v2.1.0
docker pull gcr.io/cloud-provider-vsphere/csi/release/syncer:v2.1.0
docker pull quay.io/k8scsi/csi-provisioner:v2.0.0
docker pull gcr.io/cloud-provider-vsphere/cpi/release/manager:v1.18.1
docker save -o quay.iojetstackcert-manager-cainjectorv1.11.0.tar quay.io/jetstack/cert-manager-cainjector:v1.11.0
docker save -o quay.iojetstackcert-manager-controllerv1.11.0.tar quay.io/jetstack/cert-manager-controller:v1.11.0
docker save -o quay.iojetstackcert-manager-webhookv1.11.0.tar quay.io/jetstack/cert-manager-webhook:v1.11.0
docker save -o ghcr.iokube-vipkube-vipv0.5.12.tar ghcr.io/kube-vip/kube-vip:v0.5.12
docker save -o ghcr.iokube-vipkube-vipv0.4.2.tar ghcr.io/kube-vip/kube-vip:v0.4.2
docker save -o quay.iok8scsicsi-node-driver-registrarv2.0.1.tar quay.io/k8scsi/csi-node-driver-registrar:v2.0.1
docker save -o gcr.iocloud-provider-vspherecsireleasedriverv2.1.0.tar gcr.io/cloud-provider-vsphere/csi/release/driver:v2.1.0
docker save -o quay.iok8scsilivenessprobev2.1.0.tar quay.io/k8scsi/livenessprobe:v2.1.0
docker save -o quay.iok8scsicsi-attacherv3.0.0.tar quay.io/k8scsi/csi-attacher:v3.0.0
docker save -o gcr.iocloud-provider-vspherecsireleasedriverv2.1.0.tar gcr.io/cloud-provider-vsphere/csi/release/driver:v2.1.0
docker save -o quay.iok8scsilivenessprobev2.1.0.tar quay.io/k8scsi/livenessprobe:v2.1.0
docker save -o gcr.iocloud-provider-vspherecsireleasesyncerv2.1.0.tar gcr.io/cloud-provider-vsphere/csi/release/syncer:v2.1.0
docker save -o quay.iok8scsicsi-provisionerv2.0.0.tar quay.io/k8scsi/csi-provisioner:v2.0.0
docker save -o gcr.iocloud-provider-vspherecpireleasemanagerv1.18.1.tar gcr.io/cloud-provider-vsphere/cpi/release/manager:v1.18.1
aws s3 sync ./save s3://kyoin-eks-anywhere
docker pull quay.io/jetstack/cert-manager-cainjector:v1.11.0
docker pull quay.io/jetstack/cert-manager-controller:v1.11.0
docker pull quay.io/jetstack/cert-manager-webhook:v1.11.0
docker pull ghcr.io/kube-vip/kube-vip:v0.5.12
docker pull ghcr.io/kube-vip/kube-vip:v0.4.2
docker pull quay.io/k8scsi/csi-node-driver-registrar:v2.0.1
docker pull gcr.io/cloud-provider-vsphere/csi/release/driver:v2.1.0
docker pull quay.io/k8scsi/livenessprobe:v2.1.0
docker pull quay.io/k8scsi/csi-attacher:v3.0.0
docker pull gcr.io/cloud-provider-vsphere/csi/release/driver:v2.1.0
docker pull quay.io/k8scsi/livenessprobe:v2.1.0
docker pull gcr.io/cloud-provider-vsphere/csi/release/syncer:v2.1.0
docker pull quay.io/k8scsi/csi-provisioner:v2.0.0
docker pull gcr.io/cloud-provider-vsphere/cpi/release/manager:v1.18.1
docker save -o quay.iojetstackcert-manager-cainjectorv1.11.0.tar quay.io/jetstack/cert-manager-cainjector:v1.11.0
docker save -o quay.iojetstackcert-manager-controllerv1.11.0.tar quay.io/jetstack/cert-manager-controller:v1.11.0
docker save -o quay.iojetstackcert-manager-webhookv1.11.0.tar quay.io/jetstack/cert-manager-webhook:v1.11.0
docker save -o ghcr.iokube-vipkube-vipv0.5.12.tar ghcr.io/kube-vip/kube-vip:v0.5.12
docker save -o ghcr.iokube-vipkube-vipv0.4.2.tar ghcr.io/kube-vip/kube-vip:v0.4.2
docker save -o quay.iok8scsicsi-node-driver-registrarv2.0.1.tar quay.io/k8scsi/csi-node-driver-registrar:v2.0.1
docker save -o gcr.iocloud-provider-vspherecsireleasedriverv2.1.0.tar gcr.io/cloud-provider-vsphere/csi/release/driver:v2.1.0
docker save -o quay.iok8scsilivenessprobev2.1.0.tar quay.io/k8scsi/livenessprobe:v2.1.0
docker save -o quay.iok8scsicsi-attacherv3.0.0.tar quay.io/k8scsi/csi-attacher:v3.0.0
docker save -o gcr.iocloud-provider-vspherecsireleasedriverv2.1.0.tar gcr.io/cloud-provider-vsphere/csi/release/driver:v2.1.0
docker save -o quay.iok8scsilivenessprobev2.1.0.tar quay.io/k8scsi/livenessprobe:v2.1.0
docker save -o gcr.iocloud-provider-vspherecsireleasesyncerv2.1.0.tar gcr.io/cloud-provider-vsphere/csi/release/syncer:v2.1.0
docker save -o quay.iok8scsicsi-provisionerv2.0.0.tar quay.io/k8scsi/csi-provisioner:v2.0.0
docker save -o gcr.iocloud-provider-vspherecpireleasemanagerv1.18.1.tar gcr.io/cloud-provider-vsphere/cpi/release/manager:v1.18.1
docker load -i quay.iojetstackcert-manager-cainjectorv1.11.0.tar
docker load -i quay.iojetstackcert-manager-controllerv1.11.0.tar
docker load -i quay.iojetstackcert-manager-webhookv1.11.0.tar
docker load -i ghcr.iokube-vipkube-vipv0.5.12.tar
docker load -i ghcr.iokube-vipkube-vipv0.4.2.tar
docker load -i quay.iok8scsicsi-node-driver-registrarv2.0.1.tar
docker load -i gcr.iocloud-provider-vspherecsireleasedriverv2.1.0.tar
docker load -i quay.iok8scsilivenessprobev2.1.0.tar
docker load -i quay.iok8scsicsi-attacherv3.0.0.tar
docker load -i gcr.iocloud-provider-vspherecsireleasedriverv2.1.0.tar
docker load -i quay.iok8scsilivenessprobev2.1.0.tar
docker load -i gcr.iocloud-provider-vspherecsireleasesyncerv2.1.0.tar
docker load -i quay.iok8scsicsi-provisionerv2.0.0.tar
docker load -i gcr.iocloud-provider-vspherecpireleasemanagerv1.18.1.tar
docker tag quay.io/jetstack/cert-manager-cainjector:v1.11.0 20.20.4.208/quay.io/jetstack/cert-manager-cainjector:v1.11.0
docker tag quay.io/jetstack/cert-manager-controller:v1.11.0 20.20.4.208/quay.io/jetstack/cert-manager-controller:v1.11.0
docker tag quay.io/jetstack/cert-manager-webhook:v1.11.0 20.20.4.208/quay.io/jetstack/cert-manager-webhook:v1.11.0
docker tag ghcr.io/kube-vip/kube-vip:v0.5.12 20.20.4.208/ghcr.io/kube-vip/kube-vip:v0.5.12
docker tag ghcr.io/kube-vip/kube-vip:v0.4.2 20.20.4.208/ghcr.io/kube-vip/kube-vip:v0.4.2
docker tag quay.io/k8scsi/csi-node-driver-registrar:v2.0.1 20.20.4.208/quay.io/k8scsi/csi-node-driver-registrar:v2.0.1
docker tag gcr.io/cloud-provider-vsphere/csi/release/driver:v2.1.0 20.20.4.208/gcr.io/cloud-provider-vsphere/csi/release/driver:v2.1.0
docker tag quay.io/k8scsi/livenessprobe:v2.1.0 20.20.4.208/quay.io/k8scsi/livenessprobe:v2.1.0
docker tag quay.io/k8scsi/csi-attacher:v3.0.0 20.20.4.208/quay.io/k8scsi/csi-attacher:v3.0.0
docker tag gcr.io/cloud-provider-vsphere/csi/release/driver:v2.1.0 20.20.4.208/gcr.io/cloud-provider-vsphere/csi/release/driver:v2.1.0
docker tag quay.io/k8scsi/livenessprobe:v2.1.0 20.20.4.208/quay.io/k8scsi/livenessprobe:v2.1.0
docker tag gcr.io/cloud-provider-vsphere/csi/release/syncer:v2.1.0 20.20.4.208/gcr.io/cloud-provider-vsphere/csi/release/syncer:v2.1.0
docker tag quay.io/k8scsi/csi-provisioner:v2.0.0 20.20.4.208/quay.io/k8scsi/csi-provisioner:v2.0.0
docker tag gcr.io/cloud-provider-vsphere/cpi/release/manager:v1.18.1 20.20.4.208/gcr.io/cloud-provider-vsphere/cpi/release/manager:v1.18.1
docker push 20.20.4.208/quay.io/jetstack/cert-manager-cainjector:v1.11.0
docker push 20.20.4.208/quay.io/jetstack/cert-manager-controller:v1.11.0
docker push 20.20.4.208/quay.io/jetstack/cert-manager-webhook:v1.11.0
docker push 20.20.4.208/ghcr.io/kube-vip/kube-vip:v0.5.12
docker push 20.20.4.208/ghcr.io/kube-vip/kube-vip:v0.4.2
docker push 20.20.4.208/quay.io/k8scsi/csi-node-driver-registrar:v2.0.1
docker push 20.20.4.208/gcr.io/cloud-provider-vsphere/csi/release/driver:v2.1.0
docker push 20.20.4.208/quay.io/k8scsi/livenessprobe:v2.1.0
docker push 20.20.4.208/quay.io/k8scsi/csi-attacher:v3.0.0
docker push 20.20.4.208/gcr.io/cloud-provider-vsphere/csi/release/driver:v2.1.0
docker push 20.20.4.208/quay.io/k8scsi/livenessprobe:v2.1.0
docker push 20.20.4.208/gcr.io/cloud-provider-vsphere/csi/release/syncer:v2.1.0
docker push 20.20.4.208/quay.io/k8scsi/csi-provisioner:v2.0.0
docker push 20.20.4.208/gcr.io/cloud-provider-vsphere/cpi/release/manager:v1.18.1
When a cluster creation fails, the process of cleaning up resources is manual, cumbersome and prone to errors
We could automate most of this to improve user experience when debugging.
We already have a —force-cleanup flag, it just doesn't do a lot. Think about everything you need to do when a cluster creation fails before running the cli again, that's what we should try to add to this flow. Examples:
Delete bootstrap cluster. We do that today, but it's not super robust. Find when it doesn't work and fix it.
If we don't support more than one kind cluster running, even if it's not an eks-a one, add a validation for this and give instructions to delete them
Cleanup vsphere vms if it's a vsphere cluster
Cleanup docker resources if it's a docker cluster
Delete <cluster-name> folder
# curl -Lo ./kind https://kind.sigs.k8s.io/dl/v0.10.0/kind-linux-amd64
# chmod +x ./kind
# mv ./kind /usr/bin/kind
root@eksadmin:/eks-anywhere-package# eksctl anywhere create cluster -f mgmt.yaml --bundles-override ./eks-anywhere-downloads/bundle-release.yaml
Performing setup and validations
Warning: The docker infrastructure provider is meant for local development and testing only
✅ Docker Provider setup is valid
✅ Validate OS is compatible with registry mirror configuration
✅ Validate certificate for registry mirror
✅ Validate authentication for git provider
Creating new bootstrap cluster
Error: creating bootstrap cluster: executing create cluster: ERROR: failed to create cluster: node(s) already exist for a cluster with the name "mgmt-eks-a-cluster"
, try rerunning with --force-cleanup to force delete previously created bootstrap cluster
root@eksadmin:/eks-anywhere-package# kind delete cluster --name mgmt-eks-a-cluster
Deleting cluster "mgmt-eks-a-cluster" ...
root@eksadmin:/eks-anywhere-package# eksctl anywhere create cluster -f mgmt.yaml --bundles-override ./eks-anywhere-downloads/bundle-release.yaml
Performing setup and validations
Warning: The docker infrastructure provider is meant for local development and testing only
✅ Docker Provider setup is valid
✅ Validate OS is compatible with registry mirror configuration
✅ Validate certificate for registry mirror
✅ Validate authentication for git provider
Creating new bootstrap cluster
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/plugins/v1.2.0/cni-plugins-linux-arm64-v1.2.0.tar.gz
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/plugins/v1.2.0/cni-plugins-linux-amd64-v1.2.0.tar.gz
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/etcd/v3.5.7/etcd-linux-arm64-v3.5.7.tar.gz
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/etcd/v3.5.7/etcd-linux-amd64-v3.5.7.tar.gz
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/kubernetes-client-windows-amd64.tar.gz
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/kubernetes-node-windows-amd64.tar.gz
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/kubernetes-client-darwin-amd64.tar.gz
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/kubernetes-client-linux-arm64.tar.gz
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/kubernetes-server-linux-arm64.tar.gz
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/kubernetes-node-linux-arm64.tar.gz
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/kubernetes-client-linux-amd64.tar.gz
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/kubernetes-server-linux-amd64.tar.gz
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/kubernetes-node-linux-amd64.tar.gz
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/darwin/amd64/kubectl
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/arm64/kube-apiserver
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/arm64/kube-controller-manager
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/arm64/kube-proxy
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/arm64/kube-scheduler
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/arm64/kubectl
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/arm64/kubelet
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/arm64/kubeadm
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/amd64/kube-apiserver
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/amd64/kube-controller-manager
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/amd64/kube-proxy
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/amd64/kube-scheduler
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/amd64/kubectl
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/amd64/kubelet
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/amd64/kubeadm
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/amd64/kube-apiserver.tar
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/arm64/kube-apiserver.tar
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/arm64/kube-controller-manager.tar
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/amd64/kube-scheduler.tar
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/arm64/kube-scheduler.tar
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/amd64/kube-proxy.tar
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/bin/linux/arm64/kube-proxy.tar
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/kubernetes/v1.26.4/kubernetes-src.tar.gz
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/aws-iam-authenticator/v0.6.9/aws-iam-authenticator-linux-arm64-v0.6.9.tar.gz
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/aws-iam-authenticator/v0.6.9/aws-iam-authenticator-linux-amd64-v0.6.9.tar.gz
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/aws-iam-authenticator/v0.6.9/aws-iam-authenticator-windows-amd64-v0.6.9.tar.gz
curl -O https://distro.eks.amazonaws.com/kubernetes-1-26/releases/9/artifacts/aws-iam-authenticator/v0.6.9/aws-iam-authenticator-darwin-amd64-v0.6.9.tar.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/ami/1-22/bottlerocket-v1.22.17-eks-d-1-22-27-eks-a-38-amd64.img.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/cri-tools/v1.26.0/cri-tools-linux-amd64.tar.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/etcdadm/f089d308442c18f487a52d09fd067ae9ac7cd8f2/etcdadm-linux-amd64.tar.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/image-builder/0.1.2/image-builder-linux-amd64.tar.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/ova/1-22/bottlerocket-v1.22.17-eks-d-1-22-27-eks-a-38-amd64.ova
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/raw/1-22/bottlerocket-v1.22.17-eks-d-1-22-27-eks-a-38-amd64.img.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/hook/03a67729d895635fe3c612e4feca3400b9336cc9/initramfs-x86_64
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/hook/03a67729d895635fe3c612e4feca3400b9336cc9/vmlinuz-x86_64
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/ami/1-23/bottlerocket-v1.23.17-eks-d-1-23-22-eks-a-38-amd64.img.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/cri-tools/v1.26.0/cri-tools-linux-amd64.tar.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/etcdadm/f089d308442c18f487a52d09fd067ae9ac7cd8f2/etcdadm-linux-amd64.tar.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/image-builder/0.1.2/image-builder-linux-amd64.tar.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/ova/1-23/bottlerocket-v1.23.17-eks-d-1-23-22-eks-a-38-amd64.ova
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/raw/1-23/bottlerocket-v1.23.17-eks-d-1-23-22-eks-a-38-amd64.img.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/hook/03a67729d895635fe3c612e4feca3400b9336cc9/initramfs-x86_64
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/hook/03a67729d895635fe3c612e4feca3400b9336cc9/vmlinuz-x86_64
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/ami/1-24/bottlerocket-v1.24.13-eks-d-1-24-17-eks-a-38-amd64.img.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/cri-tools/v1.26.0/cri-tools-linux-amd64.tar.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/etcdadm/f089d308442c18f487a52d09fd067ae9ac7cd8f2/etcdadm-linux-amd64.tar.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/image-builder/0.1.2/image-builder-linux-amd64.tar.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/ova/1-24/bottlerocket-v1.24.13-eks-d-1-24-17-eks-a-38-amd64.ova
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/raw/1-24/bottlerocket-v1.24.13-eks-d-1-24-17-eks-a-38-amd64.img.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/hook/03a67729d895635fe3c612e4feca3400b9336cc9/initramfs-x86_64
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/hook/03a67729d895635fe3c612e4feca3400b9336cc9/vmlinuz-x86_64
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/ami/1-25/bottlerocket-v1.25.9-eks-d-1-25-13-eks-a-38-amd64.img.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/cri-tools/v1.26.0/cri-tools-linux-amd64.tar.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/etcdadm/f089d308442c18f487a52d09fd067ae9ac7cd8f2/etcdadm-linux-amd64.tar.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/image-builder/0.1.2/image-builder-linux-amd64.tar.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/ova/1-25/bottlerocket-v1.25.9-eks-d-1-25-13-eks-a-38-amd64.ova
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/raw/1-25/bottlerocket-v1.25.9-eks-d-1-25-13-eks-a-38-amd64.img.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/hook/03a67729d895635fe3c612e4feca3400b9336cc9/initramfs-x86_64
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/hook/03a67729d895635fe3c612e4feca3400b9336cc9/vmlinuz-x86_64
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/ami/1-26/bottlerocket-v1.26.4-eks-d-1-26-9-eks-a-38-amd64.img.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/cri-tools/v1.26.0/cri-tools-linux-amd64.tar.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/etcdadm/f089d308442c18f487a52d09fd067ae9ac7cd8f2/etcdadm-linux-amd64.tar.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/image-builder/0.1.2/image-builder-linux-amd64.tar.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/ova/1-26/bottlerocket-v1.26.4-eks-d-1-26-9-eks-a-38-amd64.ova
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/raw/1-26/bottlerocket-v1.26.4-eks-d-1-26-9-eks-a-38-amd64.img.gz
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/hook/03a67729d895635fe3c612e4feca3400b9336cc9/initramfs-x86_64
curl -O https://anywhere-assets.eks.amazonaws.com/releases/bundles/38/artifacts/hook/03a67729d895635fe3c612e4feca3400b9336cc9/vmlinuz-x86_64응... 오류 나써...
controlplane이 깨져버렸당..^^;;
하나씩 올려야지... 쿠블렛인가 어디인기ㅏ ..
https://github.com/aws/eks-anywhere/issues/1629
https://anywhere.eks.amazonaws.com/docs/tasks/troubleshoot/troubleshooting/#cluster-deletion-fails-1
https://repost.aws/knowledge-center/eks-anywhere-return-cluster-upgrade-fail
처음부터 다시 시작하기
*harbor
root@ip-10-0-0-188:~# cat /etc/*release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=20.04
DISTRIB_CODENAME=focal
DISTRIB_DESCRIPTION="Ubuntu 20.04.6 LTS"
NAME="Ubuntu"
VERSION="20.04.6 LTS (Focal Fossa)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 20.04.6 LTS"
VERSION_ID="20.04"
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
VERSION_CODENAME=focal
UBUNTU_CODENAME=focal
*admin
root@ip-10-0-0-16:~# cat /etc/*release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=20.04
DISTRIB_CODENAME=focal
DISTRIB_DESCRIPTION="Ubuntu 20.04.6 LTS"
NAME="Ubuntu"
VERSION="20.04.6 LTS (Focal Fossa)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 20.04.6 LTS"
VERSION_ID="20.04"
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
VERSION_CODENAME=focal
UBUNTU_CODENAME=focal
sudo apt update
sudo apt install apt-transport-https ca-certificates curl gnupg-agent software-properties-common
curl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo apt-key add -
sudo add-apt-repository "deb [arch=amd64] https://download.docker.com/linux/ubuntu $(lsb_release -cs) stable"
sudo apt update
apt list -a docker-ce
sudo apt install docker-ce=5:20.10.0~3-0~ubuntu-focal docker-ce-cli=5:20.10.0~3-0~ubuntu-focal containerd.io
sudo usermod -aG docker $USER
root@ip-10-0-0-16:~# sudo usermod -aG docker $USER
root@ip-10-0-0-16:~# docker --version
Docker version 20.10.0, build 7287ab3
root@ip-10-0-0-188:~# docker --version
Docker version 20.10.0, build 7287ab3
mkdir /certs
cd /certs
openssl genrsa -out ca.key 4096
root@ip-10-0-0-188:/certs# openssl genrsa -out ca.key 4096
Generating RSA private key, 4096 bit long modulus (2 primes)
..++++
......................++++
e is 65537 (0x010001)
root@ip-10-0-0-188:/certs# ls
ca.key
root@ip-10-0-0-188:/certs# openssl req -x509 -new -nodes -sha512 -days 365 \
> -key ca.key \
> -out ca.crt
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:
State or Province Name (full name) [Some-State]:
Locality Name (eg, city) []:
Organization Name (eg, company) [Internet Widgits Pty Ltd]:
Organizational Unit Name (eg, section) []:
Common Name (e.g. server FQDN or YOUR name) []:10.0.0.188
Email Address []:
root@ip-10-0-0-188:/certs# openssl genrsa -out server.key 4096
Generating RSA private key, 4096 bit long modulus (2 primes)
.......................................................................................................................++++
....++++
e is 65537 (0x010001)
root@ip-10-0-0-188:/certs# openssl req -sha512 -new \
> -key server.key \
> -out server.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:
State or Province Name (full name) [Some-State]:
Locality Name (eg, city) []:
Organization Name (eg, company) [Internet Widgits Pty Ltd]:
Organizational Unit Name (eg, section) []:
Common Name (e.g. server FQDN or YOUR name) []:10.0.0.188
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:qwer1234
An optional company name []:
vi v3ext.cnf
root@ip-10-0-0-188:/certs# cat v3ext.cnf
subjectAltName = IP:10.0.0.188,IP:127.0.0.1
openssl x509 -req -sha512 -days 365 \
-extfile v3ext.cnf \
-CA ca.crt -CAkey ca.key -CAcreateserial \
-in server.csr \
-out server.crt
openssl x509 -inform PEM -in server.crt -out server.cert
cp server.cert /etc/docker/certs.d/10.0.0.188
cp server.key /etc/docker/certs.d/10.0.0.188
cp ca.crt /etc/docker/certs.d/10.0.0.188
cp server.cert /usr/local/share/ca-certificates
cp server.key /usr/local/share/ca-certificates
cp ca.crt /usr/local/share/ca-certificates
update-ca-certificates
wget https://github.com/goharbor/harbor/releases/download/v2.4.1/harbor-offline-installer-v2.4.1.tgz
tar xzvf harbor-offline-installer-v2.4.1.tgz
cp harbor.yml.tmpl harbor.yml
vi harbor.yml
# DO NOT use localhost or 127.0.0.1, because Harbor needs to be accessed by external clients.
hostname: 10.0.0.188
# http related config
http:
# port for http, default is 80. If https enabled, this port will redirect to https port
port: 80
# https related config
https:
# https port for harbor, default is 443
port: 443
# The path of cert and key files for nginx
certificate: /etc/docker/certs.d/10.0.0.188/server.cert
private_key: /etc/docker/certs.d/10.0.0.188/server.key
sudo curl -L "https://github.com/docker/compose/releases/download/1.29.2/docker-compose-$(uname -s)-$(uname -m)" -o /usr/local/bin/docker-compose
sudo chmod +x /usr/local/bin/docker-compose
sudo ln -s /usr/local/bin/docker-compose /usr/bin/docker-compose
docker-compose --version
root@ip-10-0-0-188:/harbor# docker-compose ps
Name Command State Ports
------------------------------------------------------------------------------------------------------------------------
harbor-core /harbor/entrypoint.sh Up (health: starting)
harbor-db /docker-entrypoint.sh 96 13 Up (health: starting)
harbor-jobservice /harbor/entrypoint.sh Up (health: starting)
harbor-log /bin/sh -c /usr/local/bin/ ... Up (health: starting) 127.0.0.1:1514->10514/tcp
harbor-portal nginx -g daemon off; Up (health: starting)
nginx nginx -g daemon off; Up (health: starting) 0.0.0.0:80->8080/tcp, 0.0.0.0:443->8443/tcp
redis redis-server /etc/redis.conf Up (health: starting)
registry /home/harbor/entrypoint.sh Up (health: starting)
registryctl /home/harbor/start.sh Up (health: starting)
하버 완료후 테스트 시작
root@ip-10-0-0-16:/certs# docker pull nginx
Using default tag: latest
latest: Pulling from library/nginx
f03b40093957: Pull complete
eed12bbd6494: Pull complete
fa7eb8c8eee8: Pull complete
7ff3b2b12318: Pull complete
0f67c7de5f2c: Pull complete
831f51541d38: Pull complete
Digest: sha256:af296b188c7b7df99ba960ca614439c99cb7cf252ed7bbc23e90cfda59092305
Status: Downloaded newer image for nginx:latest
docker.io/library/nginx:latest
root@ip-10-0-0-16:/certs# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
nginx latest f9c14fe76d50 5 days ago 143MB
root@ip-10-0-0-16:/certs# docker tag 10.0.0.188/nginx:latest 10.0.0.188/testproject/nginx:latest
root@ip-10-0-0-16:/certs# docker push 10.0.0.188/testproject/nginx:latest
The push refers to repository [10.0.0.188/testproject/nginx]
4fd834341303: Pushed
5e099cf3f3c8: Pushed
7daac92f43be: Pushed
e60266289ce4: Pushed
4b8862fe7056: Pushed
8cbe4b54fa88: Pushed
latest: digest: sha256:6b06964cdbbc517102ce5e0cef95152f3c6a7ef703e4057cb574539de91f72e6 size: 1571
cp server.cert /etc/docker/certs.d/10.0.0.188
cp server.key /etc/docker/certs.d/10.0.0.188
cp ca.crt /etc/docker/certs.d/10.0.0.188
root@ip-10-0-0-16:/certs# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
root@ip-10-0-0-16:/certs# docker pull 10.0.0.188/testproject/nginx:latest
latest: Pulling from testproject/nginx
f03b40093957: Pull complete
eed12bbd6494: Pull complete
fa7eb8c8eee8: Pull complete
7ff3b2b12318: Pull complete
0f67c7de5f2c: Pull complete
831f51541d38: Pull complete
Digest: sha256:6b06964cdbbc517102ce5e0cef95152f3c6a7ef703e4057cb574539de91f72e6
Status: Downloaded newer image for 10.0.0.188/testproject/nginx:latest
10.0.0.188/testproject/nginx:latest
도커 풀 성공!
EKSCTL 재설치
root@ip-10-0-0-16:/certs# snap install yq
root@ip-10-0-0-16:/certs# curl "https://github.com/weaveworks/eksctl/releases/latest/download/eksctl_$(uname -s)_amd64.tar.gz" \
> --silent --location \
> | tar xz -C /tmp
root@ip-10-0-0-16:/certs# sudo mv /tmp/eksctl /usr/local/bin/
root@ip-10-0-0-16:/certs# eksctl
The official CLI for Amazon EKS
Usage: eksctl [command] [flags]
root@ip-10-0-0-16:/certs# RELEASE_VERSION=$(curl https://anywhere-assets.eks.amazonaws.com/releases/eks-a/manifest.yaml --silent --location | yq ".spec.latestVersion")
root@ip-10-0-0-16:/certs# EKS_ANYWHERE_TARBALL_URL=$(curl https://anywhere-assets.eks.amazonaws.com/releases/eks-a/manifest.yaml --silent --location | yq ".spec.releases[] | select(.version==\"$RELEASE_VERSION\").eksABinary.$(uname -s | tr A-Z a-z).uri")
root@ip-10-0-0-16:/certs# curl $EKS_ANYWHERE_TARBALL_URL \
> --silent --location \
> | tar xz ./eksctl-anywhere
root@ip-10-0-0-16:/certs# sudo mv ./eksctl-anywhere /usr/local/bin/
root@ip-10-0-0-16:/certs# eksctl anywhere version
v0.15.4
root@ip-10-0-0-16:/certs# export OS="$(uname -s | tr A-Z a-z)" ARCH=$(test "$(uname -m)" = 'x86_64' && echo 'amd64' || echo 'arm64')
root@ip-10-0-0-16:/certs# curl -LO "https://dl.k8s.io/release/$(curl -L -s https://dl.k8s.io/release/stable.txt)/bin/${OS}/${ARCH}/kubectl"
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 138 100 138 0 0 690 0 --:--:-- --:--:-- --:--:-- 690
100 46.9M 100 46.9M 0 0 30.4M 0 0:00:01 0:00:01 --:--:-- 44.7M
root@ip-10-0-0-16:/certs# sudo mv ./kubectl /usr/local/bin
root@ip-10-0-0-16:/certs# sudo chmod +x /usr/local/bin/kubectl
root@ip-10-0-0-16:/certs# kubectl --version
error: unknown flag: --version
See 'kubectl --help' for usage.
root@ip-10-0-0-16:/certs# kubectl version
WARNING: This version information is deprecated and will be replaced with the output from kubectl version --short. Use --output=yaml|json to get the full version.
Client Version: version.Info{Major:"1", Minor:"27", GitVersion:"v1.27.2", GitCommit:"7f6f68fdabc4df88cfea2dcf9a19b2b830f1e647", GitTreeState:"clean", BuildDate:"2023-05-17T14:20:07Z", GoVersion:"go1.20.4", Compiler:"gc", Platform:"linux/amd64"}
Kustomize Version: v5.0.1
The connection to the server localhost:8080 was refused - did you specify the right host or port?
root@ip-10-0-0-16:/eks# eksctl anywhere download artifacts
root@ip-10-0-0-16:/eks# tar -xvf eks-anywhere-downloads.tar.gz
root@ip-10-0-0-16:/eks# eksctl anywhere download images -o images.tar
eksctl anywhere import images -i images.tar --bundles eks-anywhere-downloads/bundle-release.yaml --registry ${REGISTRY_ENDPOINT}
Logging in to helm registry {"registry": "10.0.0.188"}
Error: importing charts: WARNING: Using --password via the CLI is insecure. Use --password-stdin.
time="2023-05-30T02:43:31Z" level=info msg="Error logging in to endpoint, trying next endpoint" error="Get \"https://10.0.0.188/v2/\": x509: certificate signed by unknown authority"
Error: Get "https://10.0.0.188/v2/": x509: certificate signed by unknown authority
헬름 설치를 안했는데도, 알아서 되는거 보니까 안에서 내부적으로 헬름을 부르는 거같은데
도커로 컨테이너 띄워서 안에서 부를수도있지,.
근데 CA업데이트 못하겠네..^^; 그래서 —inseucre로 바꿔버렸음
eksctl anywhere import images -i images.tar --bundles eks-anywhere-downloads/bundle-release.yaml --registry ${REGISTRY_ENDPOINT} --inseucre
Tagging image {"image": "public.ecr.aws/isovalent/cilium:v1.11.15-eksa.1", "local image": "10.0.0.188/isovalent/cilium:v1.11.15-eksa.1"}
Pushing {"image": "10.0.0.188/eks-distro/kubernetes/pause:v1.26.4-eks-1-26-9"}
Pushing {"image": "10.0.0.188/isovalent/cilium:v1.11.15-eksa.1"}
Tagging image {"image": "public.ecr.aws/isovalent/operator-generic:v1.11.15-eksa.1", "local image": "10.0.0.188/isovalent/operator-generic:v1.11.15-eksa.1"}
Pushing {"image": "10.0.0.188/isovalent/operator-generic:v1.11.15-eksa.1"}
Logging in to helm registry {"registry": "10.0.0.188"}
Pushing {"chart": "tmp-eks-a-artifacts/eks-anywhere-packages-0.3.9-eks-a-38.tgz"}
Pushing {"chart": "tmp-eks-a-artifacts/tinkerbell-chart-0.2.1-eks-a-38.tgz"}
Pushing {"chart": "tmp-eks-a-artifacts/cilium-1.11.15-eksa.1.tgz"}
Pushing eks-anywhere-packages-bundles-v1-22-latest.yaml to 10.0.0.188/eks-anywhere/eks-anywhere-packages-bundles:v1-22-latest...
WARN[0435] reference for unknown type: application/vnd.unknown.config.v1+json
Pushed to 10.0.0.188/eks-anywhere/eks-anywhere-packages-bundles:v1-22-latest with digest sha256:7001dd2c4a95ad6f2e71bcaf4c1853e590a6dad64b4a3d58b363dc22c09b6efb
Pushing eks-anywhere-packages-bundles-v1-23-latest.yaml to 10.0.0.188/eks-anywhere/eks-anywhere-packages-bundles:v1-23-latest...
WARN[0436] reference for unknown type: application/vnd.unknown.config.v1+json
Pushed to 10.0.0.188/eks-anywhere/eks-anywhere-packages-bundles:v1-23-latest with digest sha256:3e8ce0a9498c368389a4a98c27d82e78ac7fc23de0be65b240a1ed8f6ab42e15
Pushing eks-anywhere-packages-bundles-v1-24-latest.yaml to 10.0.0.188/eks-anywhere/eks-anywhere-packages-bundles:v1-24-latest...
WARN[0436] reference for unknown type: application/vnd.unknown.config.v1+json
Pushed to 10.0.0.188/eks-anywhere/eks-anywhere-packages-bundles:v1-24-latest with digest sha256:fdefd8e11e5b0ab27132423d9ec21fe23e9d4b72814f0aa60ce6333a0d882e52
Pushing eks-anywhere-packages-bundles-v1-25-latest.yaml to 10.0.0.188/eks-anywhere/eks-anywhere-packages-bundles:v1-25-latest...
WARN[0436] reference for unknown type: application/vnd.unknown.config.v1+json
Pushed to 10.0.0.188/eks-anywhere/eks-anywhere-packages-bundles:v1-25-latest with digest sha256:a3ac030c04b883b38958cc7b4a38843e7d42b82b94a58e8a37661648fd264026
Pushing eks-anywhere-packages-bundles-v1-26-latest.yaml to 10.0.0.188/eks-anywhere/eks-anywhere-packages-bundles:v1-26-latest...
WARN[0436] reference for unknown type: application/vnd.unknown.config.v1+json
Pushed to 10.0.0.188/eks-anywhere/eks-anywhere-packages-bundles:v1-26-latest with digest sha256:1d293f65155a63d16275103761682ec0220e8d5ff1fa21b110f211d123ece0f8
저렇게 warn이 나오긴 하지만 일단? 되는것으로 확인.
root@ip-10-0-0-16:/eks# ^C
root@ip-10-0-0-16:/eks# eksctl anywhere create cluster -f $CLUSTER_NAME.yaml --bundles-override ./eks-anywhere-downloads/bundle-release.yaml
Performing setup and validations
Warning: The docker infrastructure provider is meant for local development and testing only
✅ Docker Provider setup is valid
✅ Validate OS is compatible with registry mirror configuration
✅ Validate certificate for registry mirror
✅ Validate authentication for git provider
Creating new bootstrap cluster
Provider specific pre-capi-install-setup on bootstrap cluster
Installing cluster-api providers on bootstrap cluster
Provider specific post-setup
Creating new workload cluster
Installing networking on workload cluster
Creating EKS-A namespace
Installing cluster-api providers on workload cluster
Installing EKS-A secrets on workload cluster
Installing resources on management cluster
Moving cluster management from bootstrap to workload cluster
Installing EKS-A custom components (CRD and controller) on workload cluster
Installing EKS-D components on workload cluster
Creating EKS-A CRDs instances on workload cluster
Installing GitOps Toolkit on workload cluster
GitOps field not specified, bootstrap flux skipped
Writing cluster config file
Deleting bootstrap cluster
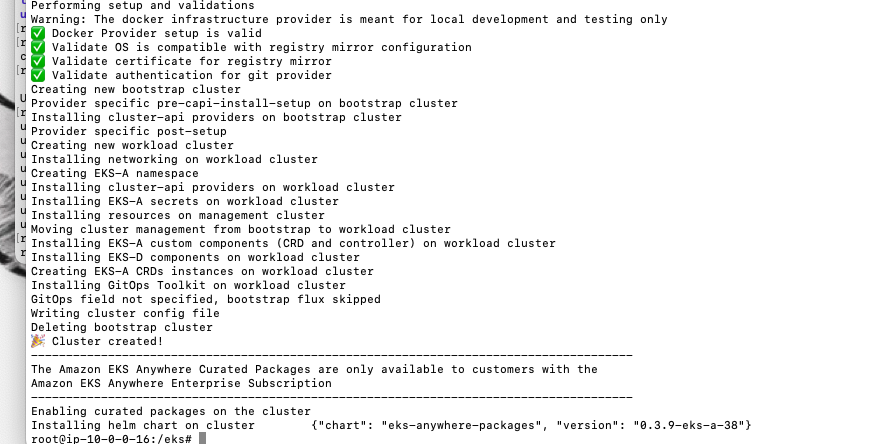
🎉 Cluster created!
--------------------------------------------------------------------------------------
The Amazon EKS Anywhere Curated Packages are only available to customers with the
Amazon EKS Anywhere Enterprise Subscription
--------------------------------------------------------------------------------------
Enabling curated packages on the cluster
Installing helm chart on cluster {"chart": "eks-anywhere-packages", "version": "0.3.9-eks-a-38"}
root@ip-10-0-0-16:/eks# docker pull public.ecr.aws/aws-containers/hello-eks-anywhere:latest
latest: Pulling from aws-containers/hello-eks-anywhere
df9b9388f04a: Pull complete
a285f0f83eed: Pull complete
e00351ea626c: Pull complete
06f5cb628050: Pull complete
32261d4e220f: Pull complete
9da77f8e409e: Pull complete
402e7ddf8d4a: Pull complete
b0fd618e2aed: Pull complete
ffbe6933fca5: Pull complete
Digest: sha256:23f79a2ea59dab9bf4c997f19c94c91954b75c5faa5463bee9f287753e5cdaf8
Status: Downloaded newer image for public.ecr.aws/aws-containers/hello-eks-anywhere:latest
public.ecr.aws/aws-containers/hello-eks-anywhere:latest
root@ip-10-0-0-16:/eks# docker pull 10.0.0.188/testproject/hello-eks-anywhere:latest
Error response from daemon: unknown: repository testproject/hello-eks-anywhere not found
root@ip-10-0-0-16:/eks# docker push 10.0.0.188/testproject/hello-eks-anywhere:latest
The push refers to repository [10.0.0.188/testproject/hello-eks-anywhere]
An image does not exist locally with the tag: 10.0.0.188/testproject/hello-eks-anywhere
root@ip-10-0-0-16:/eks# docker tag public.ecr.aws/aws-containers/hello-eks-anywhere:latest 10.0.0.188/testproject/hello-eks-anywhere:latest
root@ip-10-0-0-16:/eks# docker push 10.0.0.188/testproject/hello-eks-anywhere
Using default tag: latest
The push refers to repository [10.0.0.188/testproject/hello-eks-anywhere]
b3442f20947d: Pushed
87c14d84e57d: Pushed
bc85fd1f848a: Pushed
c0e7c94aefd8: Pushed
d6dd885da0bb: Pushed
a43749efe4ec: Pushed
45b275e8a06d: Pushed
4721bfafc708: Pushed
4fc242d58285: Pushed
latest: digest: sha256:462b9bbc4c5920f269cb562949e686477210876fe479583b8df1f5342ed70287 size: 2189
root@ip-10-0-0-16:/eks# cd ~/.docker
root@ip-10-0-0-16:~/.docker#
root@ip-10-0-0-16:/eks/mgmt# export KUBECONFIG=~/.kube/config:mgmt-eks-a-cluster.kubeconfig
kubectl create secret generic regcred --from-file=.dockerconfigjson=/root/.docker/config.json --type=kubernetes.io/dockerconfigjson
ecr-token-refresher:v0.3.9-eks-a-33 추가 반입
하도 많아서 기억안남... 수고하세요...
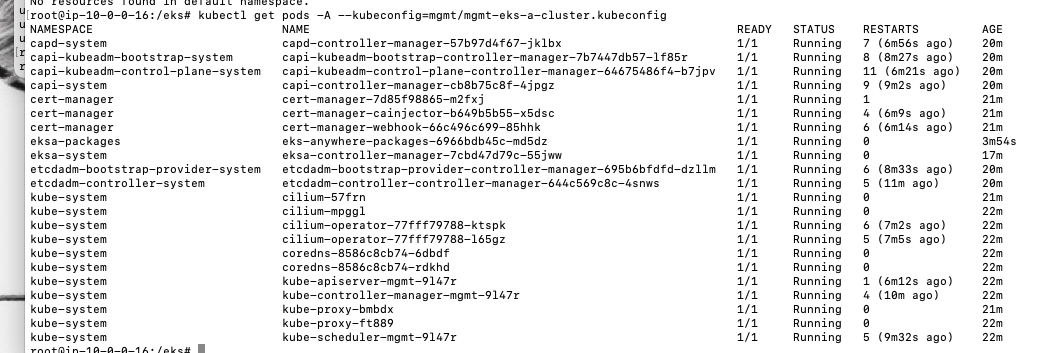
오류 :
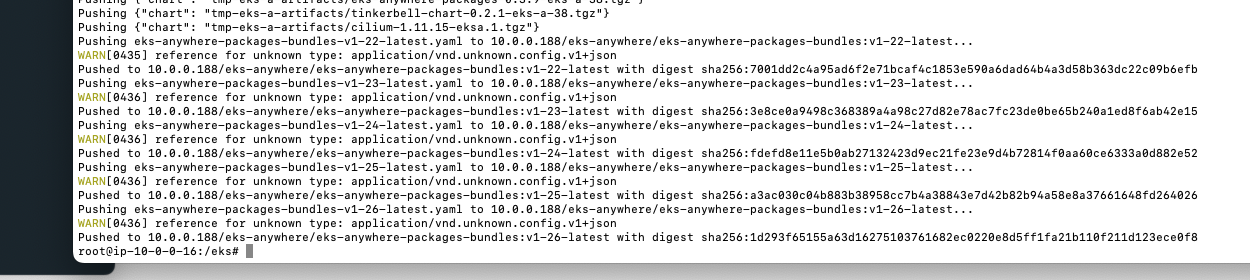
--
로컬은 실패
REDHAT으로 vSphere 올리는것은 일단 되는 것 확인... (어떤 오류가 있을지는 아직 모름)