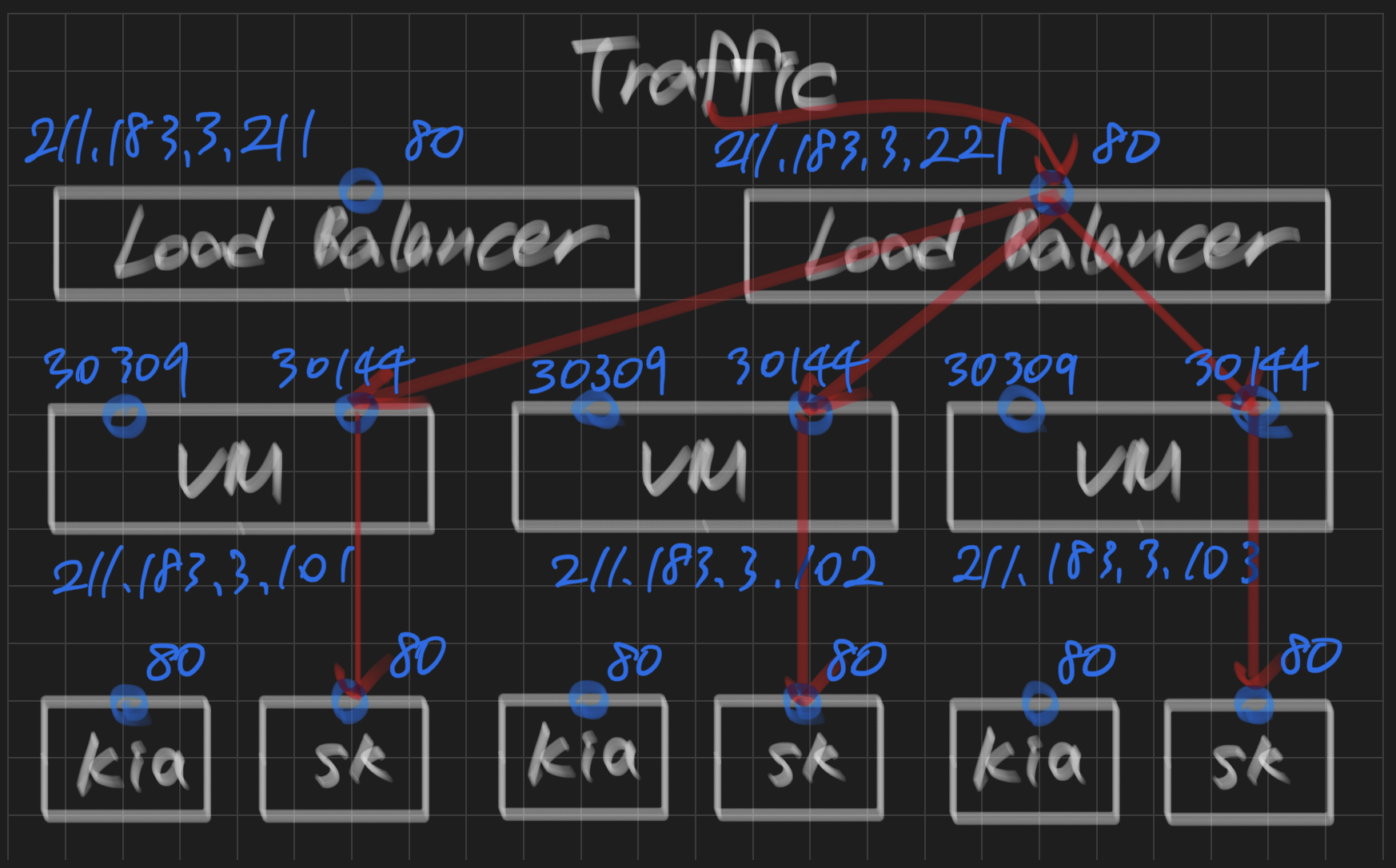
실습 1 - NFS, MetalLB
- namespace 확인
root@manager:~/k8slab# k get ns
NAME STATUS AGE
default Active 23h
kube-node-lease Active 23h
kube-public Active 23h
kube-system Active 23h
metallb-system Active 22h-> 배포했던 metallb-system이 동작 중이다.
metallb-system 배포법: http://velog.io/@ptah0414/K8S-쿠버네티스-구성하기#metallb-구성하기
- metallb-system의 pod 확인
root@manager:~/k8slab# k get pod -n metallb-system
NAME READY STATUS RESTARTS AGE
controller-66445f859d-z79gt 1/1 Running 0 22h
speaker-hrccv 1/1 Running 0 22h
speaker-lmdjk 1/1 Running 0 22h
speaker-r5rrw 1/1 Running 0 22h
speaker-r98t4 1/1 Running 0 22h- 선행 조건
- metallb가 준비된 상태이여야 한다. on-premise 환경에서 사용하기 어려운 service type LoadBalancer를 pod 형태로 제공할 수 있는 방법
- 각 LoadBalancer 별로 필요한 구성값을 추가하여 배포해야 한다.
- 생성된 pod에 볼륨을 연결할 계획이므로 mater에 nfs 서버가 구축되어 있어야 한다.
(상태 확인, 마운트 가능 여부 확인을 위해 노드에서 showmount -e 211.183.3.100을 해야 한다.)
root@worker1:~# showmount -e 211.183.3.100
Export list for 211.183.3.100:
/root/pvpvc/shared *시나리오
- 우리는 kia, sk의 서비스(Serice(nodeport/LB), Deployment, Volume)를 관리해주는 업체이다.
- kia, sk는 별도의 namespace, address-pool on LoadBalancer, mount point를 갖는다.
step 1) NFS 구성
- active 확인
root@manager:~/k8slab# systemctl status nfs-server | grep Active
Active: active (exited) since Mon 2022-09-05 17:35:38 KST; 16h ago- 디렉토리 권한 변경
root@manager:~/k8slab# mkdir /kia /sk
root@manager:~/k8slab# chmod 777 /sk -R
root@manager:~/k8slab# chmod 777 /kia -R-> -R: 디렉토리를 포함하여 하위 파일까지 모두 권한 설정
- exports 설정
root@manager:~/k8slab# vi /etc/exports /kia 211.183.3.0/24(rw,no_root_squash,sync)
/sk 211.183.3.0/24(rw,no_root_squash,sync)- nfs-server 재시작
root@manager:~/k8slab# systemctl restart nfs-server- 마운트 확인
[worker 1, 2, 3]
root@worker1:~# showmount -e 211.183.3.100
Export list for 211.183.3.100:
/sk 211.183.3.0/24
/kia 211.183.3.0/24step 2) namespace 생성
root@manager:~# mkdir lab1 ; cd lab1
root@manager:~/lab1# touch kia-ns.yaml
root@manager:~/lab1# touch sk-ns.yaml- api 버전 확인
root@manager:~/lab1# k api-resources | grep Namespace
namespaces ns v1 false Namespace- kia namespace를 위한 yaml 작성
root@manager:~/lab1# vi kia-ns.yaml apiVersion: v1
kind: Namespace
metadata:
name: kia- 배포 및 확인
root@manager:~/lab1# k apply -f kia-ns.yaml
namespace/kia created
root@manager:~/lab1# k get ns | grep kia
kia Active 6s- sk도 마찬가지 방식으로 배포
root@manager:~/lab1# cp kia-ns.yaml sk-ns.yaml
root@manager:~/lab1# vi sk-ns.yaml apiVersion: v1
kind: Namespace
metadata:
name: skroot@manager:~/lab1# k apply -f sk-ns.yaml
namespace/sk created
root@manager:~/lab1# k get ns | grep sk
sk Active 7sstep 3) metallb를 이용하여 사용하게 될 LB의 주소 대역 지정하기(ConfigMap)
default: 211.183.3.201 - 211.183.3.210
kia : 211.183.3.211 - 211.183.3.220
sk : 211.183.3.221 - 211.183.3.230 root@manager:~/lab1# vi lb-config.yaml apiVersion: v1
kind: ConfigMap
metadata:
namespace: metallb-system # metallb의 namespace에 작성해서 config로 넘김
name: config
data:
config: | # config에게 넘길 내용
address-pools:
- name: default
protocol: layer2
addresses:
- 211.183.3.201-211.183.3.210
- name: kia
protocol: layer2
addresses:
- 211.183.3.211-211.183.3.220
- name: sk
protocol: layer2
addresses:
- 211.183.3.221-211.183.3.230- ConfigMap 배포
root@manager:~/lab1# k apply -f lb-config.yaml
configmap/config created
root@manager:~/lab1# step 4) 각 회사별 deployment와 svc 배포
참고 : https://metallb.universe.tf/usage/
root@manager:~/k8slab# vi kia-deploy-svc.yaml apiVersion: apps/v1
kind: Deployment
metadata:
namespace: kia # NameSpace
name: kia-deploy
spec: # Replcaset 설정
strategy:
type: Recreate # Rolling Update 방식이 아닌 Recreate 방식
replicas: 3
selector: # 아래의 label 개수를 확인하여 pod 관리
matchLabels:
app: kia # label은 app: kia
template: # Pod 구성
metadata:
labels:
app: kia
spec: # 컨테이너 구성
containers:
- name: kia-nginx # 컨테이너 이름
image: nginx
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
namespace: kia
name: kia-lb
annotations:
metallb.universe.tf/address-pool: kia
spec:
ports:
- port: 80
targetPort: 80
selector:
app: kia
type: LoadBalancer- 배포 및 확인
root@manager:~/k8slab# k get pod,svc -n kia
NAME READY STATUS RESTARTS AGE
pod/kia-deploy-5fcb8b68db-ft6qd 1/1 Running 2 31m
pod/kia-deploy-5fcb8b68db-t2hxg 1/1 Running 0 31m
pod/kia-deploy-5fcb8b68db-vhjh9 1/1 Running 1 31m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/kia-lb LoadBalancer 10.104.64.119 211.183.3.211 80:30309/TCP 28s-> 211.183.3.211가 할당되었음
- 위와 동일한 방법으로 sk도 배포
root@manager:~/k8slab# cp kia-deploy-svc.yaml sk-deploy-svc.yaml
root@manager:~/k8slab# vi sk-deploy-svc.yaml apiVersion: apps/v1
kind: Deployment
metadata:
namespace: sk # NameSpace
name: sk-deploy
spec: # Replcaset 설정
strategy:
type: Recreate # Rolling Update 방식이 아닌 Recreate 방식
replicas: 3
selector: # 아래의 label 개수를 확인하여 pod 관리
matchLabels:
app: sk # label은 app: kia
template: # Pod 구성
metadata:
labels:
app: sk
spec: # 컨테이너 구성
containers:
- name: sk-nginx # 컨테이너 이름
image: httpd
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
namespace: sk
name: sk-lb
annotations:
metallb.universe.tf/address-pool: sk
spec:
ports:
- port: 80
targetPort: 80
selector:
app: sk
type: LoadBalancer- 배포
root@manager:~/k8slab# k apply -f sk-deploy-svc.yaml
deployment.apps/sk-deploy created
service/sk-lb created- 확인
root@manager:~/k8slab# k get pod,svc -n sk
NAME READY STATUS RESTARTS AGE
pod/sk-deploy-848bb96648-bng5c 1/1 Running 0 45s
pod/sk-deploy-848bb96648-cm4m9 1/1 Running 0 45s
pod/sk-deploy-848bb96648-gcbnk 1/1 Running 0 45s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/sk-lb LoadBalancer 10.96.246.199 211.183.3.221 80:30144/TCP 2m26s-> 211.183.3.221기 할당되었음
step 5) pod 마운트 구성
deploy 배포시 kia와 sk의 모든 포드는 각 포드의 /test 디렉토리를 각각 nfs 서버의 /kia, /sk 와 마운트되어야 한다.
확인해야할 사항
kubectl exec [pod 이름] -n kia -- ls /test
kia.txt가 보여야 한다.
- yaml 수정
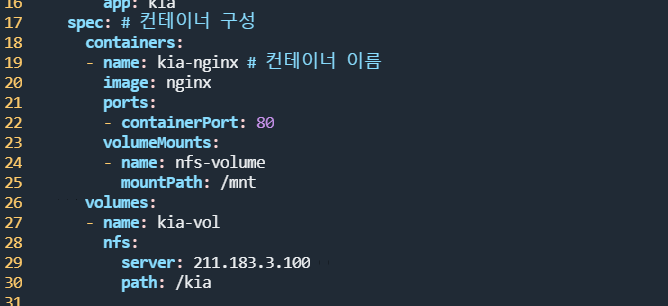
root@manager:~/k8slab# vi kia-deploy-svc.yaml spec: # 컨테이너 구성
containers:
- name: kia-nginx # 컨테이너 이름
image: nginx
ports:
- containerPort: 80
volumeMounts:
- name: kia-vol
mountPath: /test
volumes:
- name: kia-vol
nfs:
server: 211.183.3.100
path: /kia-> nginx 컨테이너와 볼륨을 위와 같이 설정
- 배포
root@manager:~/k8slab# k apply -f kia-deploy-svc.yaml
deployment.apps/kia-deploy configured
service/kia-lb unchanged- 배포 확인
root@manager:~/k8slab# k get pod -n kia
NAME READY STATUS RESTARTS AGE
kia-deploy-5ccc6dc745-2hn7r 1/1 Running 0 49s
kia-deploy-5ccc6dc745-j4scd 1/1 Running 0 49s
kia-deploy-5ccc6dc745-svwbg 1/1 Running 0 49s- 임의의 파일 생성
root@manager:~/k8slab/lab1# touch /kia/kia.txt
root@manager:~/k8slab/lab1# touch /sk/sk.txt- pod에서 마운트 확인
root@manager:~/k8slab# k exec kia-deploy-5ccc6dc745-2hn7r -n kia -- ls /test
kia.txt-> nfs-server에서 생성한 파일을 kia pod에서 볼 수 있다.
- sk도 마찬가지 방법으로 배포
root@manager:~/k8slab# k get pod -n sk -w
NAME READY STATUS RESTARTS AGE
sk-deploy-7c96d8bf46-74tzx 1/1 Running 0 13s
sk-deploy-7c96d8bf46-jvxnn 1/1 Running 0 13s
sk-deploy-7c96d8bf46-s7kqw 1/1 Running 0 13s- pod에서 마운트 확인
root@manager:~/k8slab# k exec sk-deploy-7c96d8bf46-74tzx -n sk -- ls /test
sk.txt-> nfs-server에서 생성한 파일을 sk pod에서 볼 수 있다.
Metallb의 ip 지정하기
root@manager:~/k8slab/lab1# vi kia-deploy-svc.yaml spec:
ports:
- port: 80
targetPort: 80
selector:
app: kia
type: LoadBalancer
loadBalancerIP: 211.183.3.215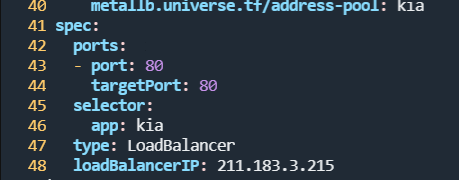
root@manager:~/k8slab# k apply -f kia-deploy-svc.yaml
deployment.apps/kia-deploy unchanged
service/kia-lb configured
root@manager:~/k8slab# k get pod,svc -n kia
NAME READY STATUS RESTARTS AGE
pod/kia-deploy-5ccc6dc745-2hn7r 1/1 Running 0 103m
pod/kia-deploy-5ccc6dc745-j4scd 1/1 Running 0 103m
pod/kia-deploy-5ccc6dc745-svwbg 1/1 Running 0 103m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/kia-lb LoadBalancer 10.104.64.119 211.183.3.215 80:30309/TCP 149m-> 211.183.3.215
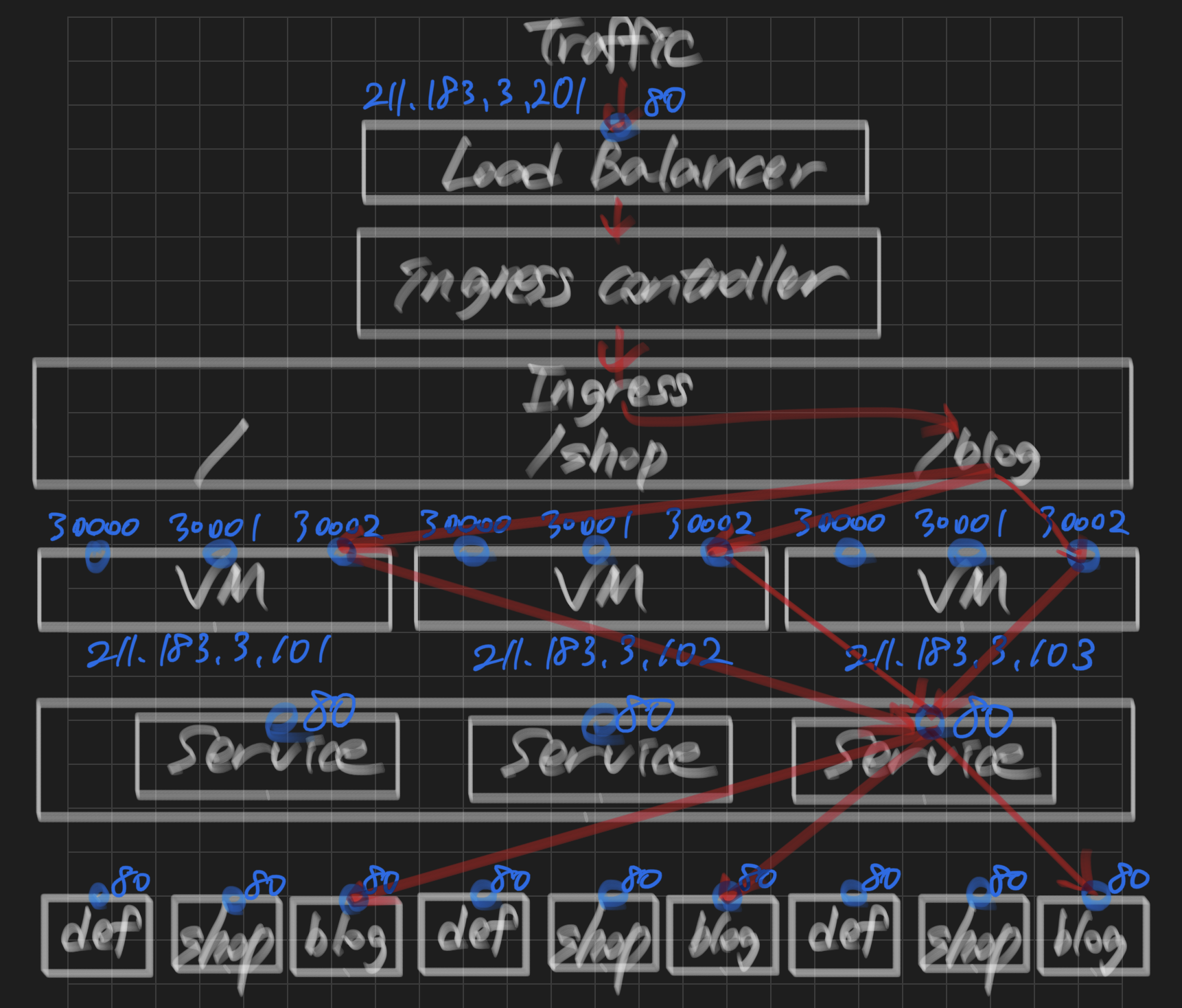
실습 2 - Ingress
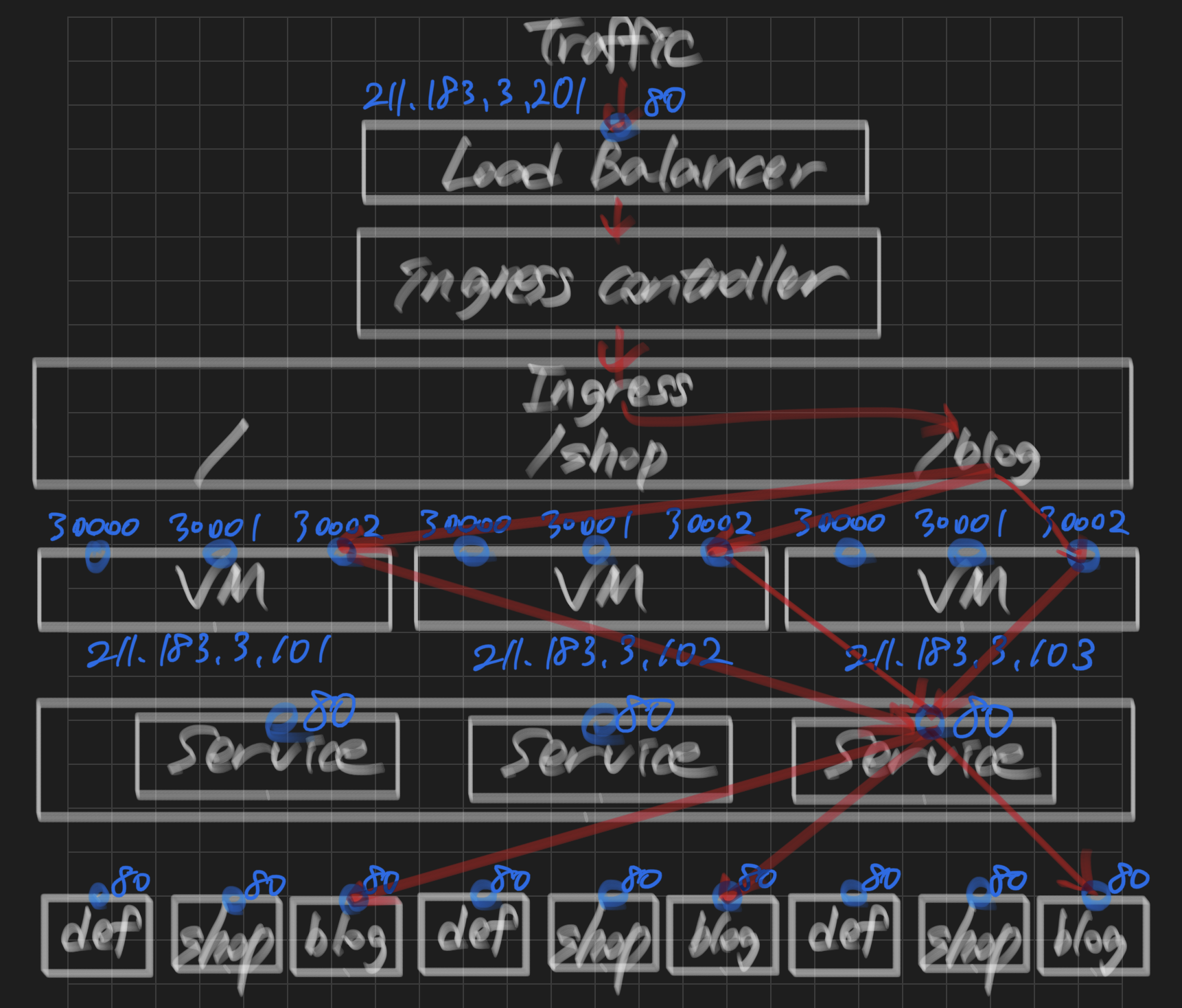

lb-ingress-service를 이용한 웹서비스 환경 배포
- api 버전 확인
root@manager:~/k8slab/lab2# k api-resources | grep Ingress
ingresses ing extensions/v1beta1 true Ingress
ingressclasses networking.k8s.io/v1 false IngressClass
ingresses ing networking.k8s.io/v1 true Ingressstep 1) ingress의 yaml 작성
- 각 웹페이지의 도메인을 설정한다.
- /
- /shop
- /blog
root@manager:~/k8slab# mkdir lab2 ; cd lab2
root@manager:~/k8slab/lab2# vi ingress-config.yaml apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-nginx # ingress 명
annotations:
nginx.ingress.kubernetes.io/rewrite-target: /
kubernetes.io/ingress.class: "nginx"
spec:
rules:
- http:
paths:
- path: / # 기본 디렉토리
pathType: Prefix
backend:
service:
name: default # 서비스 이름
port:
number: 80 # nodePort Service의 포트 번호
- path: /shop
pathType: Prefix
backend:
service:
name: shop
port:
number: 80
- path: /blog
pathType: Prefix
backend:
service:
name: blog
port:
number: 80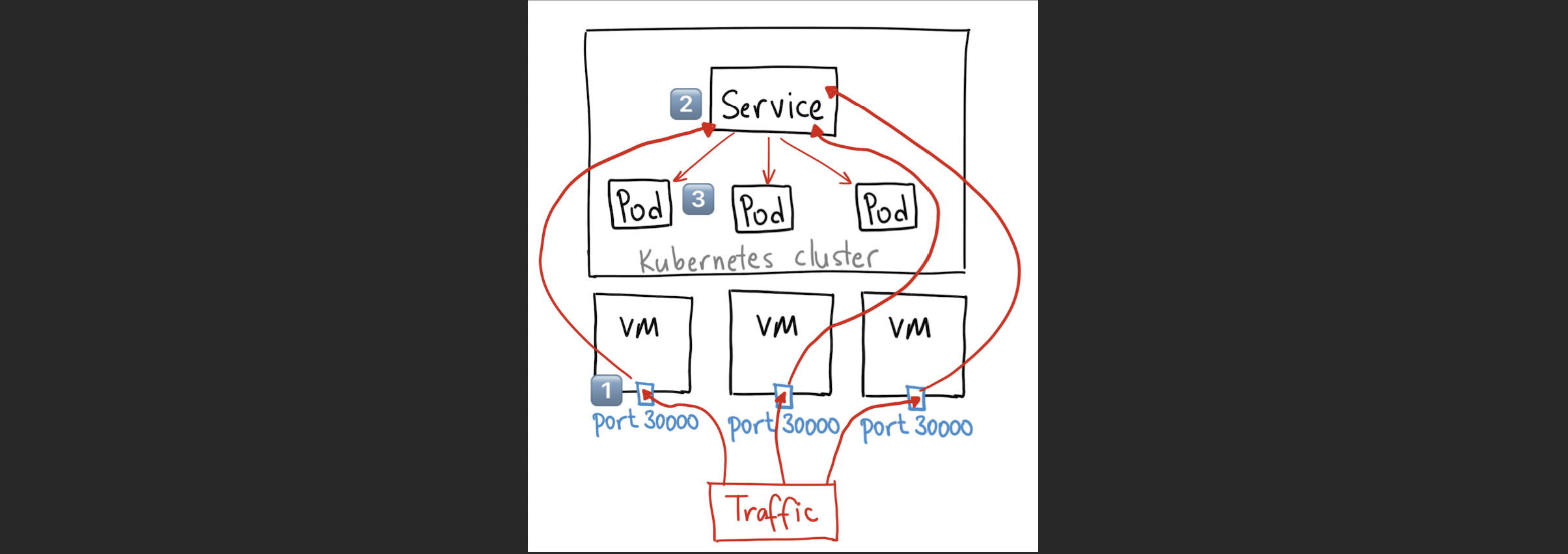
step 2) ingress controller 배포
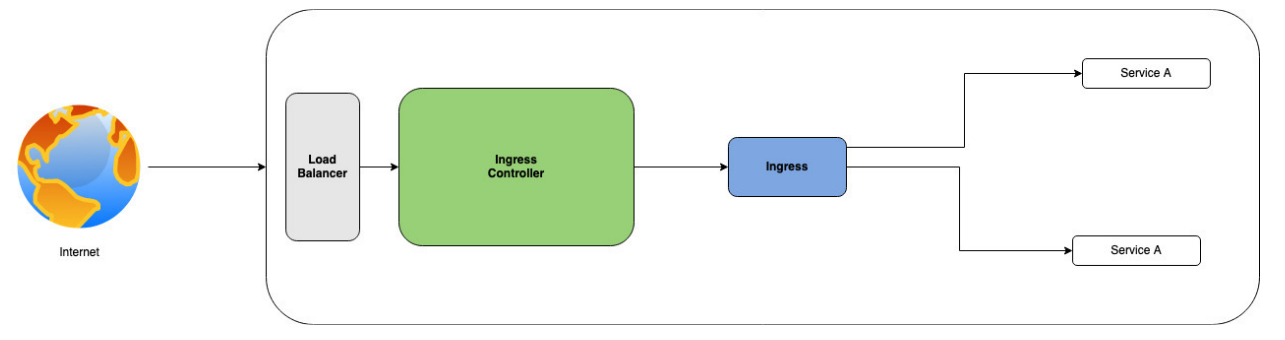
root@manager:~/k8slab# kubectl apply -f \
> https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.1.2/deploy/static/provider/cloud/deploy.yaml
namespace/ingress-nginx created
serviceaccount/ingress-nginx created
serviceaccount/ingress-nginx-admission created
role.rbac.authorization.k8s.io/ingress-nginx created
role.rbac.authorization.k8s.io/ingress-nginx-admission created
clusterrole.rbac.authorization.k8s.io/ingress-nginx created
clusterrole.rbac.authorization.k8s.io/ingress-nginx-admission created
rolebinding.rbac.authorization.k8s.io/ingress-nginx created
rolebinding.rbac.authorization.k8s.io/ingress-nginx-admission created
clusterrolebinding.rbac.authorization.k8s.io/ingress-nginx created
clusterrolebinding.rbac.authorization.k8s.io/ingress-nginx-admission created
configmap/ingress-nginx-controller created
service/ingress-nginx-controller created
service/ingress-nginx-controller-admission created
deployment.apps/ingress-nginx-controller created
job.batch/ingress-nginx-admission-create created
job.batch/ingress-nginx-admission-patch created
ingressclass.networking.k8s.io/nginx created
validatingwebhookconfiguration.admissionregistration.k8s.io/ingress-nginx-admission created
root@manager:~/k8slab# step 3) shop, blog, default 페이지의 yaml 작성
root@manager:~/k8slab/lab2# touch shop-deploy-svc.yaml
root@manager:~/k8slab/lab2# touch blog-deploy-svc.yaml
root@manager:~/k8slab/lab2# touch default-deploy-svc.yaml- shop yaml 작성
root@manager:~/k8slab/lab2# vi shop-deploy-svc.yaml apiVersion: apps/v1
kind: Deployment
metadata:
name: shop
spec:
replicas: 3
selector:
matchLabels:
app: shop
template: # 컨테이너 내용
matadata:
name: shop
labels:
app: shop
spec:
containers:
- name: shop
image: nginx
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
name: shop # backend Service의 이름과 같아야 함
spec:
ports:
- name: shop-port
port: 80 # service의 포트
targetPort: 80 # pod의 포트
nodePort: 30001
selector:
app: shop
type: NodePort참고:
https://velog.io/@ptah0414/K8S-쿠버네티스-구성하기#step-4-nginx-deployment와-loadbalancer-service-배포
https://velog.io/@ptah0414/K8S-쿠버네티스-2#nodeport-service-배포
- 마찬가지 방법으로 default와 blog의 yaml도 작성
default: 포트 30000, nginx
shop: 포트 30001, nginx
blog: 포트 30002, httpd
step 4) shop, blog, default 배포
root@manager:~/k8slab/lab2# k apply -f shop-deploy-svc.yaml
deployment.apps/shop created
service/shop created
root@manager:~/k8slab/lab2# k apply -f blog-deploy-svc.yaml
deployment.apps/blog created
service/blog created
root@manager:~/k8slab/lab2# k apply -f default-deploy-svc.yaml
deployment.apps/default created
service/default created- 접속 확인
root@manager:~/k8slab/lab2# curl http://211.183.3.101:30000
<!DOCTYPE html>
<html>
<head>
<title>Welcome to nginx!</title>
<style>
html { color-scheme: light dark; }
body { width: 35em; margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif; }
</style>
</head>
<body>
<h1>Welcome to nginx!</h1>
<p>If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.</p>
<p>For online documentation and support please refer to
<a href="http://nginx.org/">nginx.org</a>.<br/>
Commercial support is available at
<a href="http://nginx.com/">nginx.com</a>.</p>
<p><em>Thank you for using nginx.</em></p>
</body>
</html>
root@manager:~/k8slab/lab2# curl http://211.183.3.101:30001
<!DOCTYPE html>
<html>
<head>
<title>Welcome to nginx!</title>
<style>
html { color-scheme: light dark; }
body { width: 35em; margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif; }
</style>
</head>
<body>
<h1>Welcome to nginx!</h1>
<p>If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.</p>
<p>For online documentation and support please refer to
<a href="http://nginx.org/">nginx.org</a>.<br/>
Commercial support is available at
<a href="http://nginx.com/">nginx.com</a>.</p>
<p><em>Thank you for using nginx.</em></p>
</body>
</html>
root@manager:~/k8slab/lab2# curl http://211.183.3.101:30002
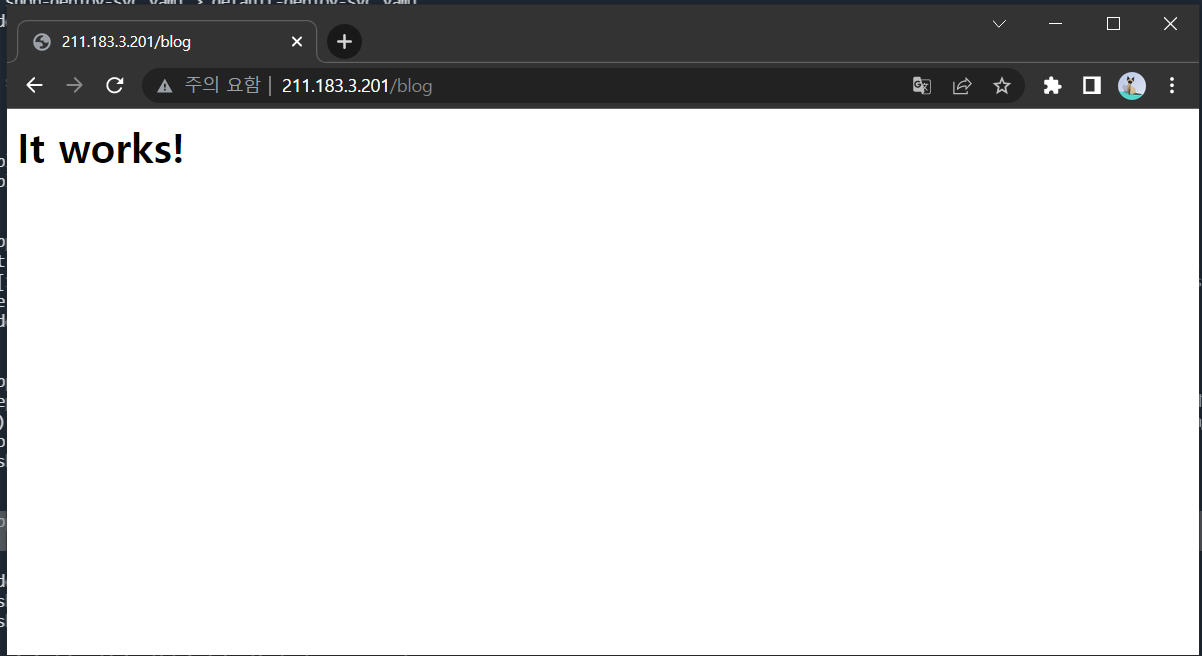
<html><body><h1>It works!</h1></body></html>step 5) ingress 배포
root@manager:~/k8slab/lab2# k apply -f ingress-config.yaml
ingress.networking.k8s.io/ingress-nginx created- ingress 배포 확인
root@manager:~/k8slab/lab2# k get ing -w
NAME CLASS HOSTS ADDRESS PORTS AGE
ingress-nginx <none> * 211.183.3.201 80 38s-> 211.183.3.201
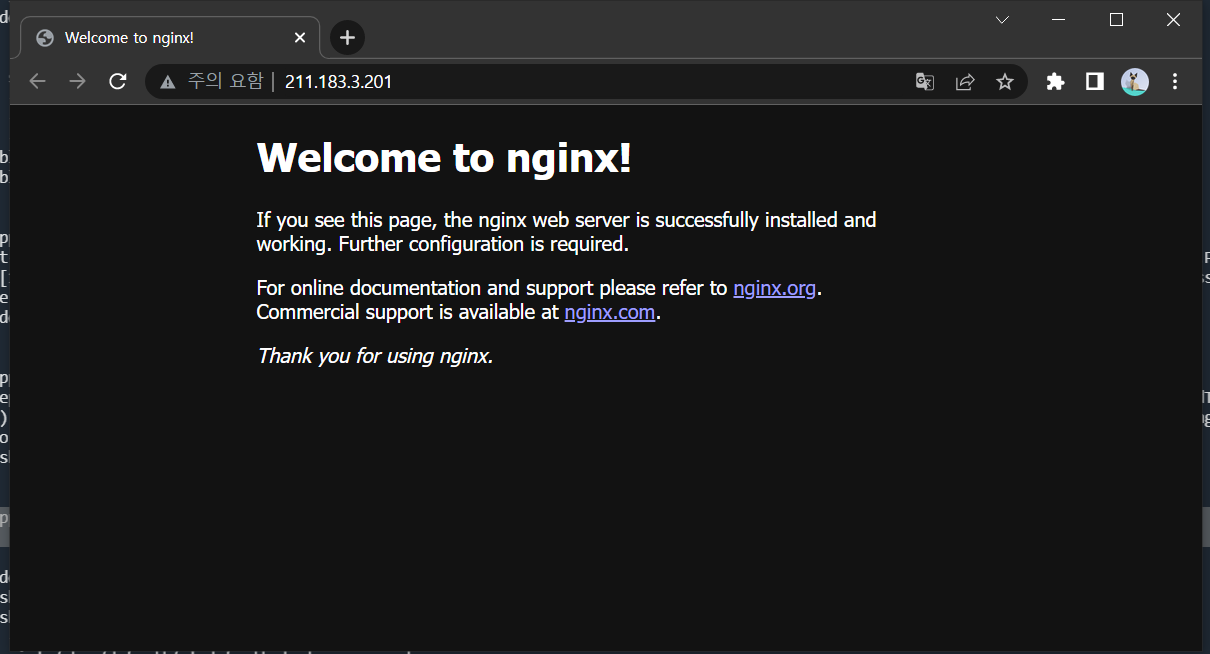
step 6) 각 페이지 접속
루트 페이지 접속(default)
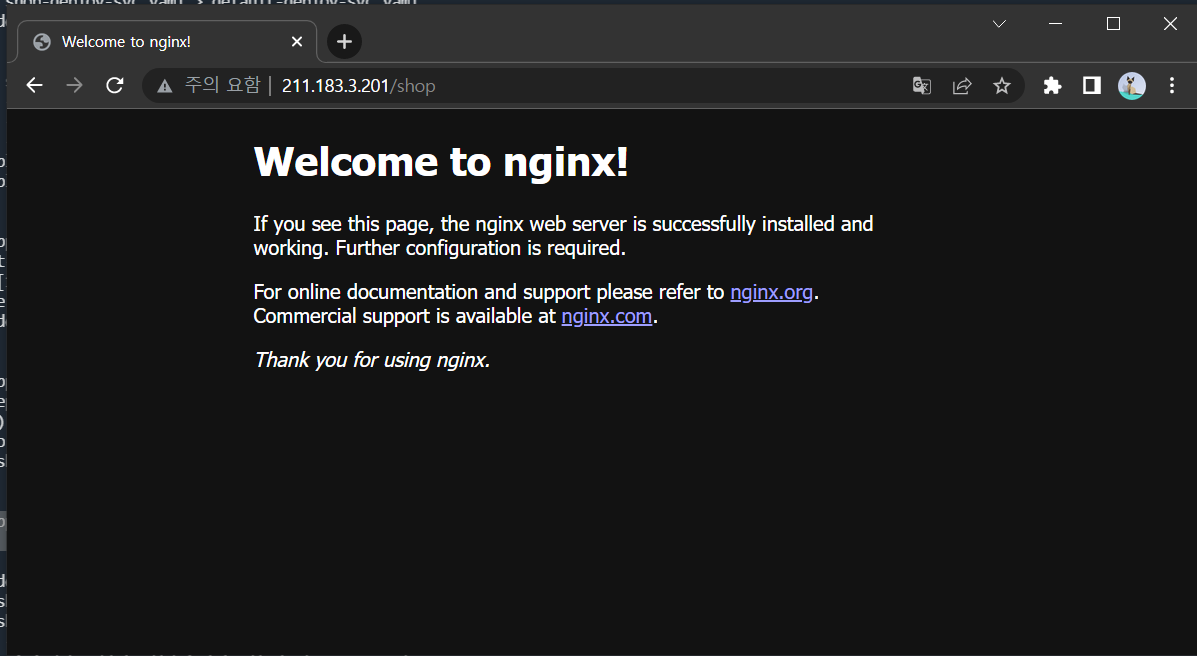
shop 페이지 접속
blog 페이지 접속
실습 3 - 파일을 ConfigMap으로 작성
시나리오
우리 회사 DNS 서버에 아래의 정보를 등록시켜둔다.
test.com -> zone 파일 -> test.com.db
www IN A 211.183.3.99
user1 IN A 211.183.3.201 -> user1.test.com zone 파일 구성
https://velog.io/@ptah0414/Linux-22-07-22-TIL#zone-파일-구성
별도의 도메인을 구매하여 해당 도메인과 211.183.3.201을 매핑
configMap 생성
https://velog.io/@ptah0414/K8S-쿠버네티스-구성하기#configmap-생성
configMapRef를 통한 배포
https://velog.io/@ptah0414/K8S-쿠버네티스-구성하기#방법-1-configmapref을-통한-배포
volume을 통한 configMap 배포
https://velog.io/@ptah0414/K8S-쿠버네티스-구성하기#방법-2-configmap을-볼륨처럼-이용하여-pod의-특정-파일과-마운트-시키기
각각의 페이지를 configmap을 이용하여 붙여넣기 해보기
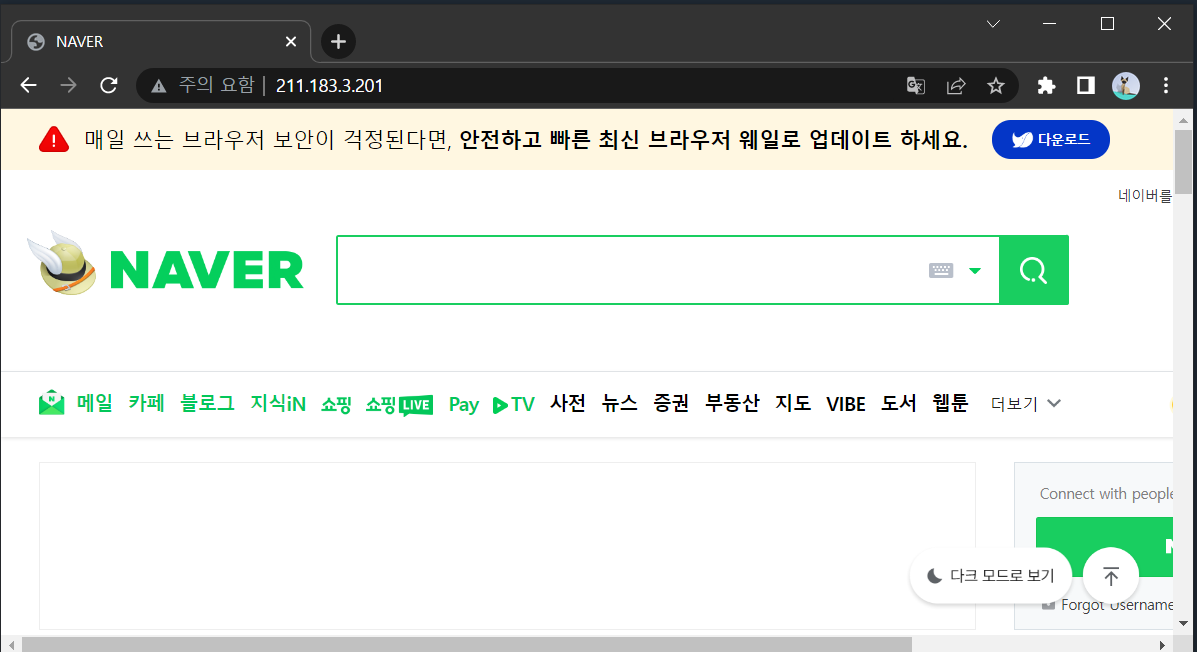
default(nginx) -> naver 페이지 (https://naver.com)
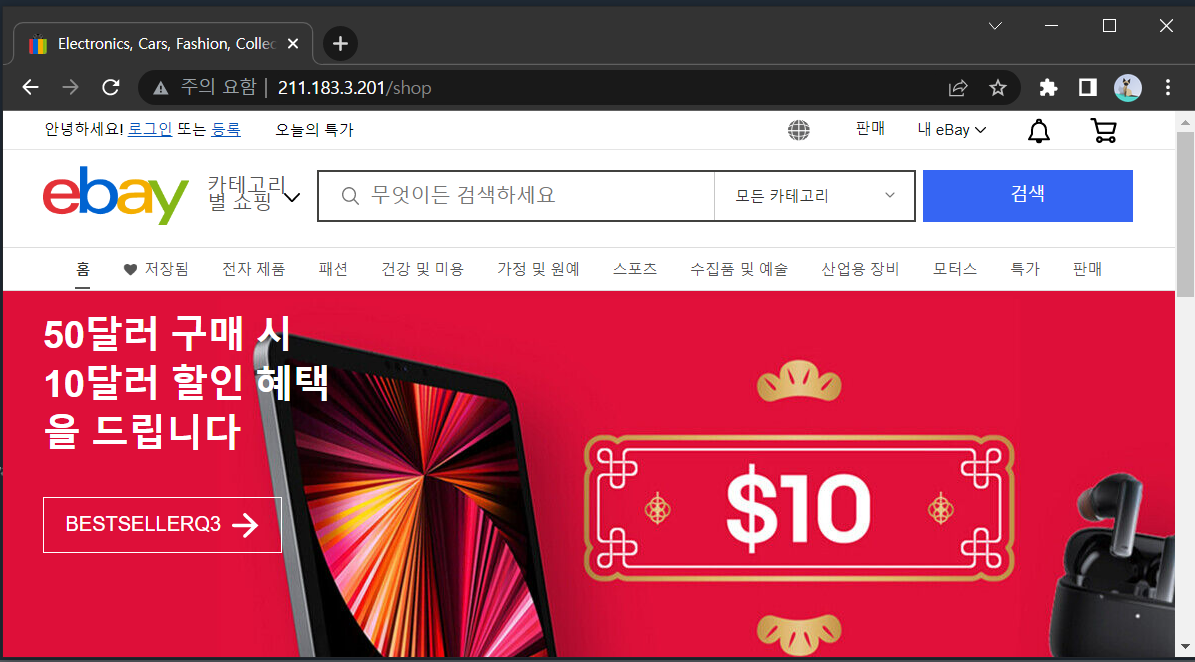
shop(nginx) -> ebay 페이지 (https://ebay.com)
blog(httpd) -> instagram 페이지 (https://instagram.com)step 1) index.html 생성
root@manager:~/k8slab/lab2/default# curl "https://www.naver.com" > index.html
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 133k 0 133k 0 0 25572 0 --:--:-- 0:00:05 --:--:-- 29219root@manager:~/k8slab/lab2/shop# curl "https://www.ebay.com" > index.html
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 257k 0 257k 0 0 349k 0 --:--:-- --:--:-- --:--:-- 349kroot@manager:~/k8slab/lab2/blog# curl -L "https://www.instagram.com/" > index.html
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 101k 100 101k 0 0 97817 0 0:00:01 0:00:01 --:--:-- 97817- 생성 확인
root@manager:~/k8slab/lab2# tree
.
├── blog
│ ├── blog-deploy-svc.yaml
│ └── index.html
├── default
│ ├── default-deploy-svc.yaml
│ └── index.html
├── ingress-config.yaml
└── shop
├── index.html
└── shop-deploy-svc.yamlstep 2) configmap 생성 (defaultcm, shopcm, blogcm)
root@manager:~/k8slab/lab2/blog# k create cm blogcm --from-file index.html
configmap/blogcm created
root@manager:~/k8slab/lab2/blog# cd ..
root@manager:~/k8slab/lab2# cd shop/
root@manager:~/k8slab/lab2/shop# k create cm shopcm --from-file index.html
configmap/shopcm created
root@manager:~/k8slab/lab2/shop# cd ..
root@manager:~/k8slab/lab2# cd default/
root@manager:~/k8slab/lab2/default# k create cm defaultcm --from-file index.html
configmap/defaultcm createdstep 3) yaml 에 ConfigMap 추가 후 배포
root@manager:~/k8slab/lab2/default# vi default-deploy-svc.yaml spec:
containers:
- name: default
image: nginx
ports:
- containerPort: 80
volumeMounts:
- name: defaultvol
mountPath: /usr/share/nginx/html
volumes:
- name: defaultvol
configMap:
name: defaultcm- default 배포
root@manager:~/k8slab/lab2/default# k apply -f default-deploy-svc.yaml
deployment.apps/default configured
service/default unchangedstep 4) 접속
- blog yaml에 config 추가
root@manager:~/k8slab/lab2/blog# vi blog-deploy-svc.yaml spec:
containers:
- name: blog
image: httpd
ports:
- containerPort: 80
volumeMounts:
- name: blogvol
mountPath: /usr/local/apache2/htdocs
volumes:
- name: blogvol
configMap:
name: blogcm- blog 배포
root@manager:~/k8slab/lab2/blog# k apply -f blog-deploy-svc.yaml
deployment.apps/blog configured
service/blog unchanged- blog 접속

- shop yaml에 config 추가
root@manager:~/k8slab/lab2/shop# vi shop-deploy-svc.yaml spec:
containers:
- name: shop
image: nginx
ports:
- containerPort: 80
volumeMounts:
- name: shopvol
mountPath: /usr/share/nginx/html
volumes:
- name: shopvol
configMap:
name: shopcm- shop 배포
root@manager:~/k8slab/lab2/shop# k apply -f shop-deploy-svc.yaml
deployment.apps/shop configured
service/shop unchanged- shop 접속
실습 4 - Secret
- 일반적인 사용법은 configMap과 거의 동일하지만, 저장된 secret을 describe를 통해 확인할 수는 없다.
- ssh, key, 인증서, username/password 등을 pod 내에 전달할 때 주로 사용한다.
- 사설 저장소를 사용하는 경우 각 노드는 사설 저장소로 접속하기 위한 인증 정보를 보유하고 있어야 한다. 인증 정보에 포함되는 요소들은 username, password, 저장소의 주소가 필요하다.
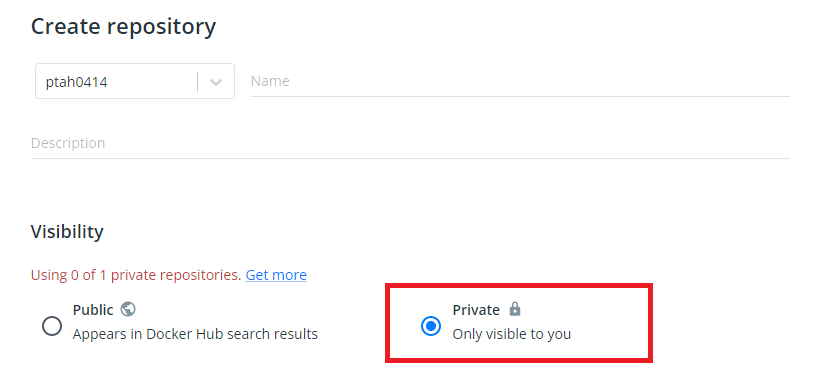
- secret은 노드 간 통신에서는 보이지 않지만 pod 내에서는 plain text로 확인이 된다.
도커 허브로의 로그인을 위한 secret 생성하기
step 1) secret 생성 (dockerhub1)
root@manager:~# kubectl create secret generic dockerhub1 \
>--from-file=.dockerconfigjson=/root/.docker/config.json \
>--type=kubernetes.io/dockerconfigjson
secret/dockerhub1 created- secret 확인 (dockerhub1)
root@manager:~# k get secret
NAME TYPE DATA AGE
default-token-qjcn4 kubernetes.io/service-account-token 3 31h
dockerhub1 kubernetes.io/dockerconfigjson 1 18sstep 2) yaml 작성 (dockerhub1 사용해서 컨테이너 image pull)
root@manager:~# vi testoracle.yaml apiVersion: v1
kind: Pod
metadata:
name: private-reg
spec:
containers:
- name: test-oracle
image: oraclelinux:9-slim
imagePullSecrets:
- name: dockerhub1step 3) 배포
root@manager:~# k apply -f testoracle.yaml
pod/private-reg created- 배포 확인
root@manager:~# k get pod -w
NAME READY STATUS RESTARTS AGE
private-reg 1/1 Running 0 11m기타
KUBECONFIG
root@manager:~/k8slab# echo $KUBECONFIG
/etc/kubernetes/admin.conf KUBECONFIG는 service account의 정보를 누구로 할 것인지 파일을 지정하는 변수
만약 변수 선언이 안 되어있다면
export KUBECONFIG=/etc/kubernetes/admin.confexport: 전역 변수로 선언
/etc/kubernetes/admin.conf: 쿠버네티스 전체 관리자 admin
배포 모두 삭제
root@manager:~/k8slab# kubectl delete -f .
serviceaccount "metrics-server" deleted
clusterrole.rbac.authorization.k8s.io "system:aggregated-metrics-reader" deleted
clusterrole.rbac.authorization.k8s.io "system:metrics-server" deleted
rolebinding.rbac.authorization.k8s.io "metrics-server-auth-reader" deleted
clusterrolebinding.rbac.authorization.k8s.io "metrics-server:system:auth-delegator" deleted
clusterrolebinding.rbac.authorization.k8s.io "system:metrics-server" deleted
service "metrics-server" deleted
deployment.apps "metrics-server" deleted
apiservice.apiregistration.k8s.io "v1beta1.metrics.k8s.io" deleted
configmap "config" deleted
namespace "rapa" deleted
deployment.apps "nginx-deployment" deleted
service "nginx-lb" deleted
Error from server (NotFound): error when deleting "autoscaletest.yaml": deployments.apps "autoscaletest" not found
Error from server (NotFound): error when deleting "autoscaletest.yaml": services "nginx3-lb" not found
Error from server (NotFound): error when deleting "cmtestpod.yaml": pods "cmtestpod" not found
Error from server (NotFound): error when deleting "cmtestpodvol.yaml": pods "cmtestpodvol" not found
Error from server (NotFound): error when deleting "nfs-pod.yaml": pods "nfs-pod" not found
Error from server (NotFound): error when deleting "nginx2-deploy-svc.yaml": deployments.apps "nginx2-deployment" not found
Error from server (NotFound): error when deleting "nginx2-deploy-svc.yaml": services "nginx2-lb" not found
잘 보고 가요!!