
Introduction
Recently, I checked the web security of our MVP(Minimum viable project) using the ZAP,open source web scanner, and it reported some issues obviously.
While I'am fixing the issues, I going to learn about the causes, solutions, what it could affect on.
Issue
1. Path Traversal
What is the path traversal?
Path traversal (Directory path traversal) is the attack which request abnormal file path by adding
../
The attackers can access the file system which is out of the web by adding ../ to the requests.
This issue is simple and well known to the developer, there are lots of variations.
- Microsoft Windows
- Percent encoding in URIs
Solutions
REFERENCE : WIKI-Directory-traversal-attack
2. CSP (Content-Security-Policy)
What is the CSP?
Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types of attacks, including Cross-Site Scripting (XSS) and data injection attacks.
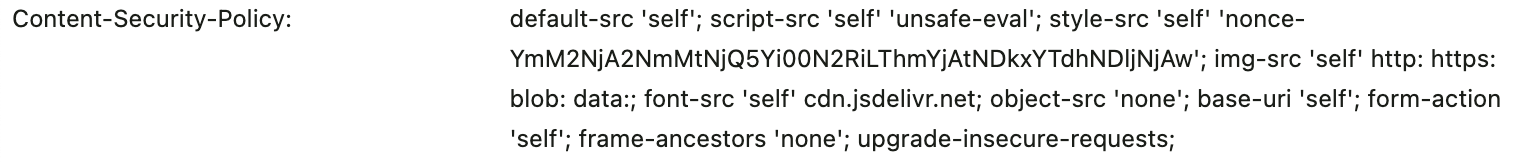
We got issue because there is no content-security-policy info on headers.
Solutions
There are lots of ways to add Content-Security-Policy based on project & framework.
EX) <meta http-equiv="Content-Security-Policy" content="default-src 'self'; img-src https://*; child-src 'none'; ..." /> to the header.
But, I faced CSP of style-src problem which is related Nextjs and Tailwind.
Here is the Link.
3. Missing Anti-clickjacking Header
What is the clickjacking?
Clickjacking is when an attacker uses multiple transparent or opaque layers to trick a user into clicking on a button or link on another page when they were intending to click on the top level page.
According to the Clickjacking, a transparent top level page or layer should be rendered to the service by injecting script.
Solution
Add optionX-Frame-Options : SAMEORIGIN to the headers.
REFERENCE :
What is the Clickjacking(OWASP)
4. Server Leaks Information via "X-Powered-By" HTTP Response Header Field(s)
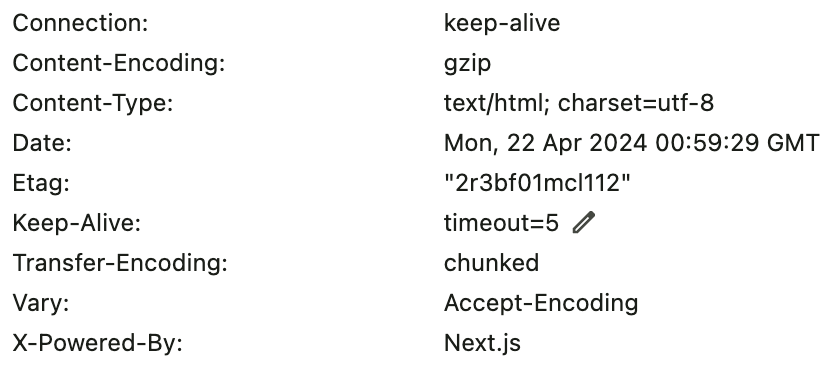
What is the X-Powered-By?
The X-Powered-By header describes the technologies used by the webserver.
What is the problem?
If the X-Powered-By is opened and the weak point of that server is known well, lots of attackers will attack the weak point of the web service through there.
Just hiding X-Powered-By, getting better security.
And also, I can't find any advatages for revealing the X-Powered-By information. Then why don't they who create the browser hide X-Powered-By as a default option.
Anyway...
Solution
It will be solved by just hiding X-Powered-By.
REFERENCE : WIKI-Directory-traversal-attack
5. Strict-Transport-Security Header Not Set
What is the (HTTP) Strict Transport Security?
It is also called HTTP Strict Transport Security(HSTS).
The HTTP Strict-Transport-Security response header informs browsers that the site should only be accessed using HTTPS, and that any future attempts to access it using HTTP should automatically be converted to HTTPS.
On Development, this problem came from request to the endpoint which don't have SSL.
Solution
Just applying SSL to the Server, it will be gone.
6. Timestamp Disclosure - Unix
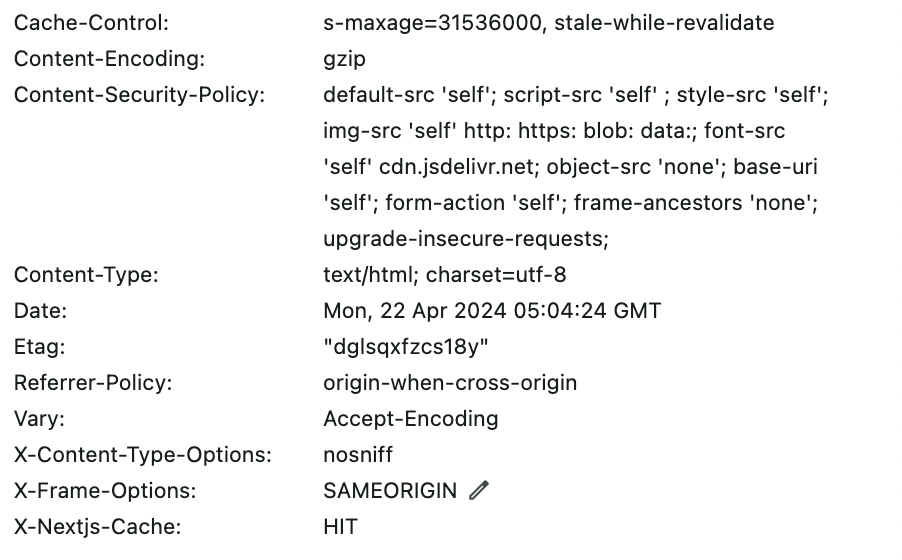
7. X-Content-Type-Options Header Missing
The X-Content-Type-Options response HTTP header is a marker used by the server to indicate that the MIME types advertised in the Content-Type headers should be followed and not be changed. The header allows you to avoid MIME type sniffing by saying that the MIME types are deliberately configured.
*MIME types (IANA media types) : MDN_MIME_TYPE
This problem came from the setting fo X-Content-Type-Options on Response Header.
By setting directives as a nosniff, it blocks a request if the request destination is of type style and the MIME type is not text/css, or of type script and the MIME type is not a JavaScript MIME type.
REFERENCE : X-Content-Type-Options Header Missing
