
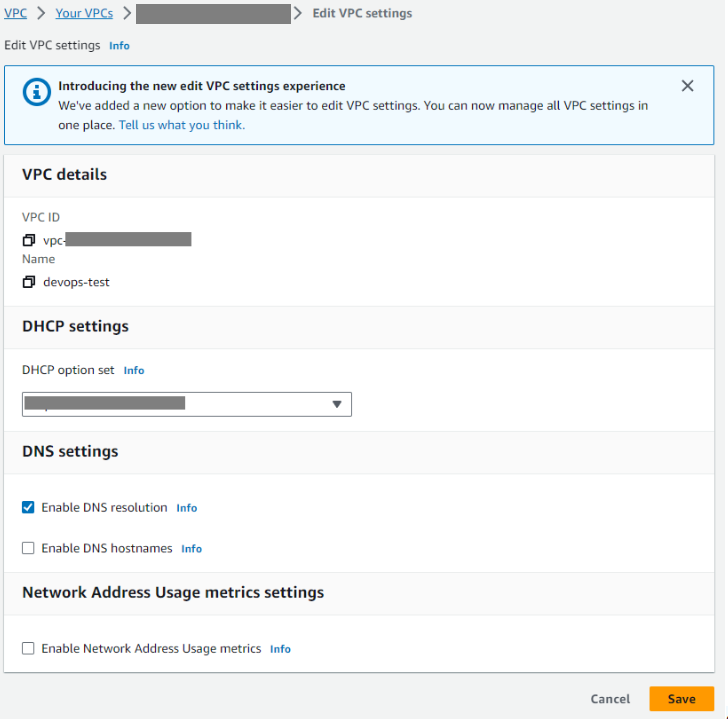
VPC 생성
- name: devops-test
- Enable DNS resolution : Enable
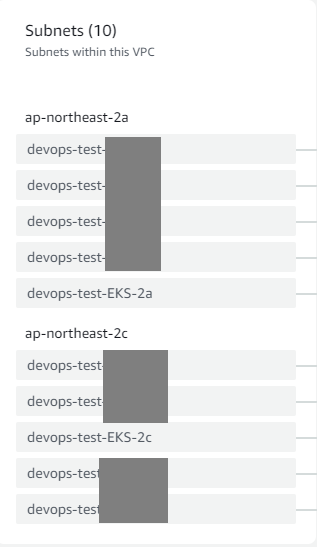
Subnet 구성 정보
- AZ 2개
Bastion 생성
- instance type
- t3.medium
- security group 생성
- name
- devops-bastion-sg
- name
- network 설정
- vpc
- devops-test
- subnet
- dmz-2c
- vpc
- keypair 생성
- type : pem
- name
- devops-bastion

Bastion 접속 및 계정 생성
생성한 key pair pem 파일 통해 ssh 접속
devops 계정 생성 및 암호 설정
sudo useradd devopssudo passwd devops
[ec2-user@ip-172-28-21-245 ~]$ sudo useradd devops
[ec2-user@ip-172-28-21-245 ~]$
[ec2-user@ip-172-28-21-245 ~]$
[ec2-user@ip-172-28-21-245 ~]$ sudo passwd devops
Changing password for user devops.
New password:
Retype new password:
passwd: all authentication tokens updated successfully.
작업 후 접속 했으나 접속이 안됨..
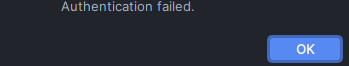
- 조치
- ec2 iam role 추가 후 접속 확인

- ec2 iam role 추가 후 접속 확인
eksctl 설치
eksctl download for unix 가이드 참고하여 진행
설치
# for ARM systems, set ARCH to: `arm64`, `armv6` or `armv7`
ARCH=amd64
PLATFORM=$(uname -s)_$ARCH
curl -sLO "https://github.com/eksctl-io/eksctl/releases/latest/download/eksctl_$PLATFORM.tar.gz"
# (Optional) Verify checksum
curl -sL "https://github.com/eksctl-io/eksctl/releases/latest/download/eksctl_checksums.txt" | grep $PLATFORM | sha256sum --check
tar -xzf eksctl_$PLATFORM.tar.gz -C /tmp && rm eksctl_$PLATFORM.tar.gz
sudo mv /tmp/eksctl /usr/local/bin확인
[devops@ip-172-28-21-245 ~]$ eksctl version
0.160.0cluster 생성 / Nodegroup 생성
cluster, nodegroup 모두 clsuter.yaml 파일 하나로 관리
core nodegroup 과 ci nodegroup 분리
eksctl create cluster -f cluster.yaml
apiVersion: eksctl.io/v1alpha5
kind: ClusterConfig
metadata:
name: eks-devops-cluster-10
region: ap-northeast-2
version: "1.27"
vpc:
subnets:
private:
ap-northeast-2a:
id: {your-subnet-id-2a}
ap-northeast-2c:
id: {your-subnet-id-2c}
nat:
gateway: Disable
iam:
serviceRoleARN: {your-cluste-role-iam-arn}
privateCluster:
enabled: true
# additionalEndpointServices:
# For Cluster Autoscaler
# - "autoscaling"
# endpoint 기존에 존재 하기 때문에 스킵 ( 중복 안됨 )
skipEndpointCreation: true
managedNodeGroups:
- name: devops-core-nodegroup
instanceType: t3.large
instanceName: devops-core-nodegroup
desiredCapacity: 2
taints:
- key: devops.node-role
value: "core"
effect: NoExecute
ssh:
publicKeyName: devops-eks-nodegroup
privateNetworking: true
subnets: [{your-subnet-id-2a},{your-subnet-id-2c}]
labels: {
devops.role: core
}
iam:
instanceRoleARN: {your-nodegroup-iam-arn}
- name: devops-ci-nodegroup
instanceType: t3.large
instanceName: devops-ci-nodegroup
desiredCapacity: 2
ssh:
publicKeyName: devops-eks-nodegroup
privateNetworking: true
subnets: [{your-subnet-id-2a},{your-subnet-id-2c}]
labels: {
devops.role: worker,
devops.type: ci
}
iam:
instanceRoleARN: {your-nodegroup-iam-arn}
- 진행중
- cloudformation 통해 Cluster 생성 진행 확인 가능
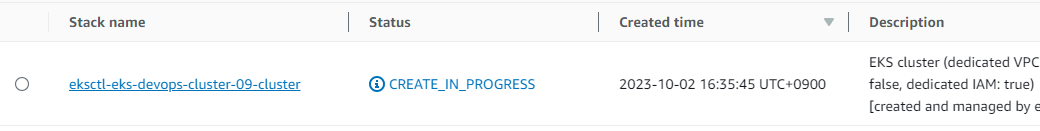
- cloudformation 통해 Cluster 생성 진행 확인 가능
- 완료
- 약 9분 소요

